GrrCon 2016 DFIR Write up - Part 1
CTF HOMEPAGE https://ir.e-corp.biz/home
To start off, get Volatility or a prebuilt vm like SANS SIFT Workstation, they've recommended using the provided Security Onion image. Also, check out the community plugin repo for Volatility.
Download CTF files - specifically NSM.zip
** SPOILER ALERT **
Level 1
Question 1)
First lets find out what started the shit storm on his computer! What is the c2 address of the malware? (this case involves the host IP 10.1.1.122 of Phillip Price)
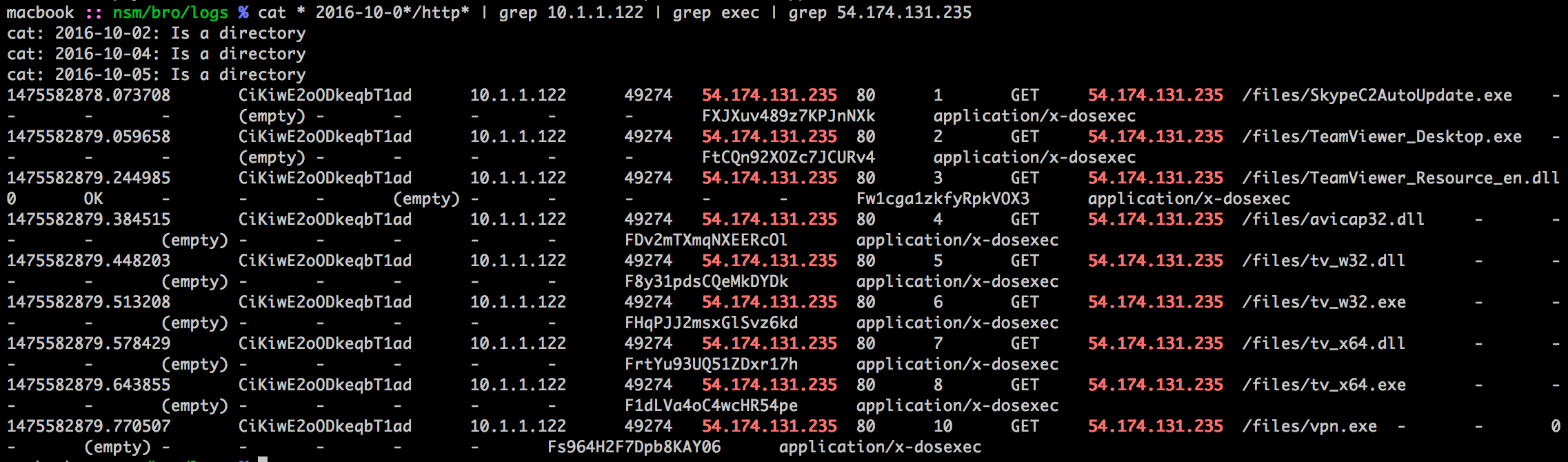
I decided to go at the Bro log files.
cat * 2016-10-0*/http* | grep 10.1.1.122
Answer: 54.174.131.235
Question 2)
What is the User Agent string of the malware?
From the same log as above it provides the full user agent string.
Answer: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.116 Safari/537.36
Question 3)
What is the AV common name Used by Kasperskyfor the delivered malware? (Case doesn't matter some times there is more than one name used by av vendors so try alt names if you're sure or message me) Example: darkrat Update: I'm going through the answers of this once in a while to check to see if those are close I will mark it correct.
cat * 2016-10-0*/http* | grep 10.1.1.122 | grep 54.174.131.235 | grep exe
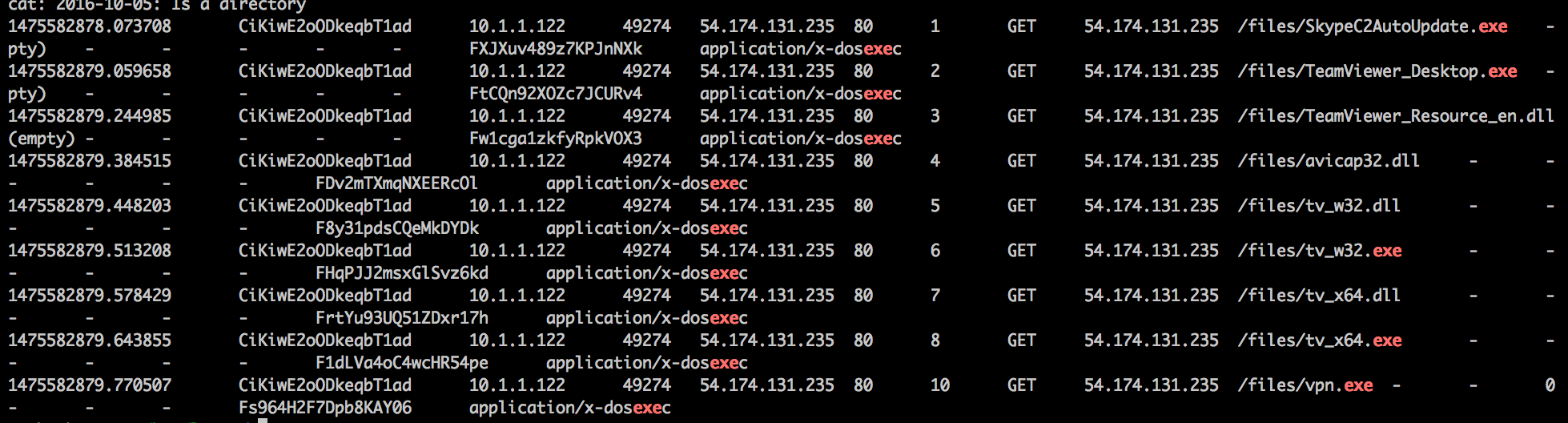
Check out the Bro extracted files...
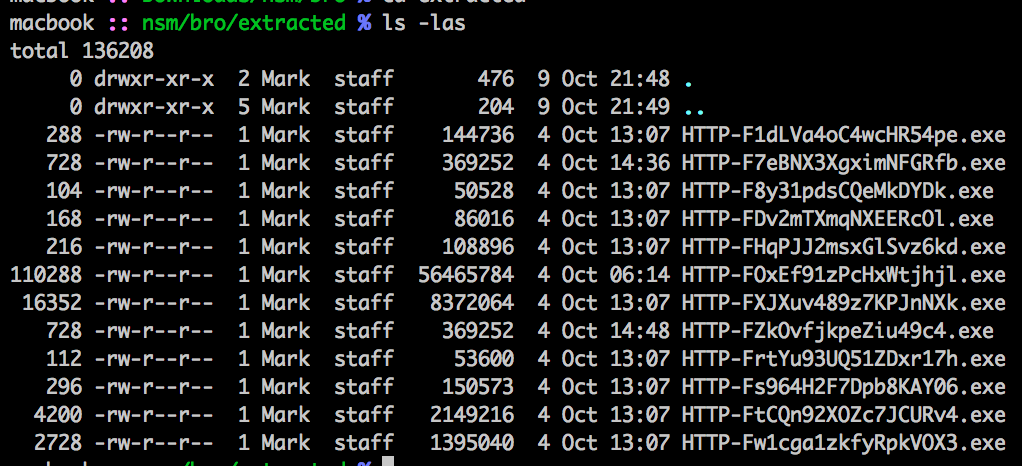
open them up in VirtualTotal OS X Uploader
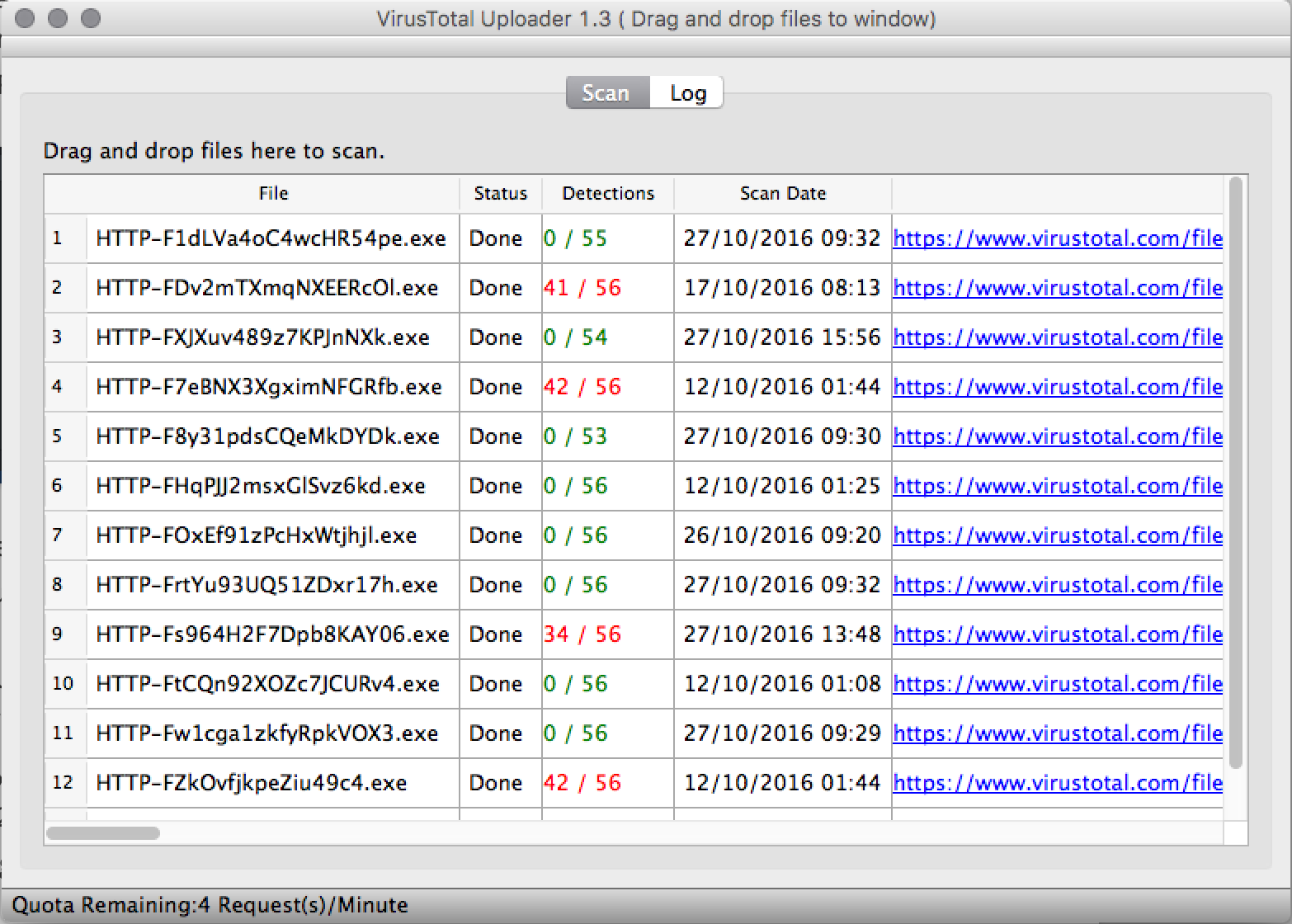
Looking into the ones highlighted as malicious. 2 of the files had the same file hash (f33cb6aeaba31c6ffff19872b3d53f364a3ff934e728cb3e0e771e2372fae6b2) and were detailed as AVUpdates. This left me with
-
avicap32.dll.x-msdos-program https://www.virustotal.com/en/file/285ea9c44a3cbb488ac4558c777dbdf6f01c0917dc2c04254d008dac9ce2dda5/analysis/1476692005/
Looking at the Kaspersky AV names, Trojan-Spy.Win32.Teamspy.aa stands out and there are numerous articles about a Teamviewer malware with that name.
Answer: teamspy
Question 4)
What is the malware version?
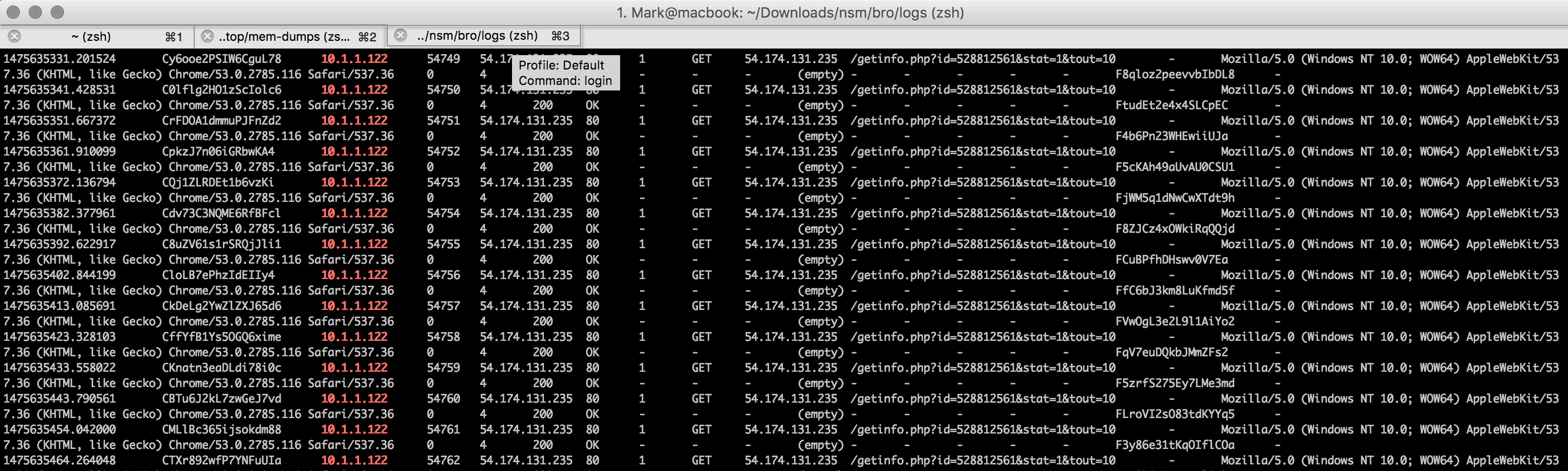
Using the same bro logs you can see a request which is different to the rest
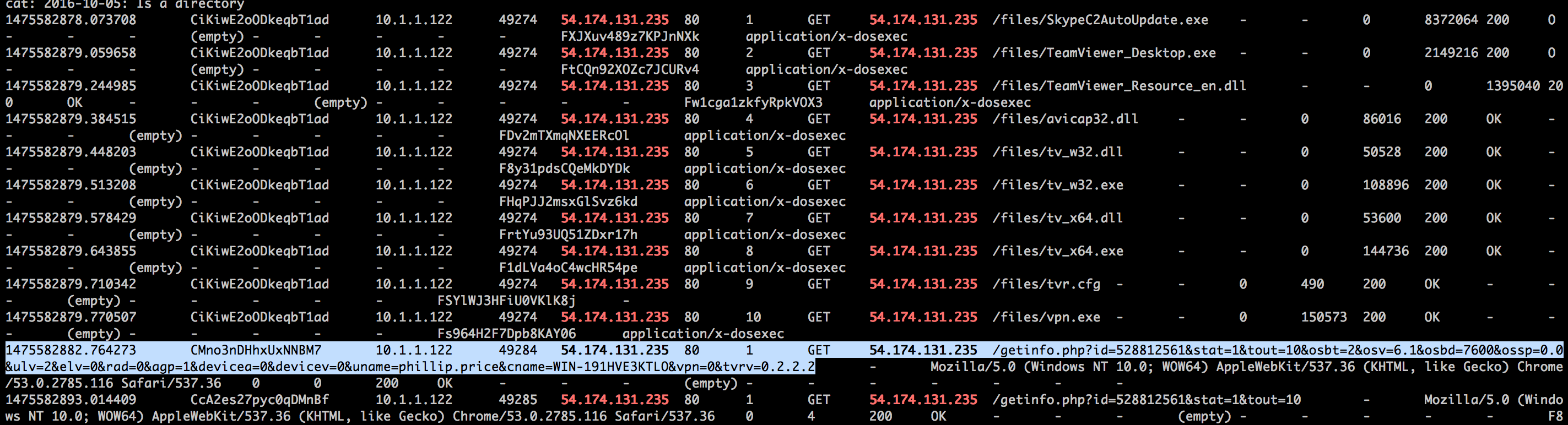
Bro http.log string
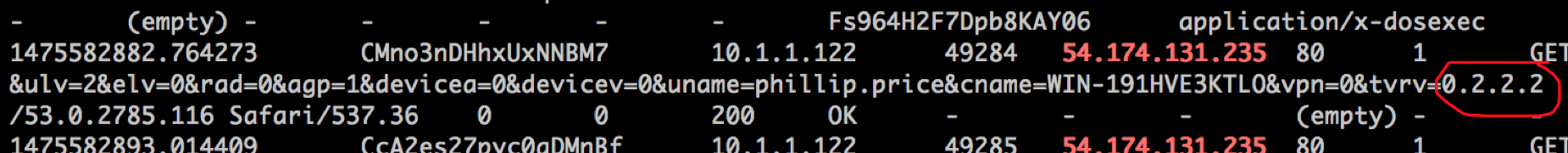
1475582882.764273 CMno3nDHhxUxNNBM7 10.1.1.122 49284 54.174.131.235 80 1 GET 54.174.131.235 /getinfo.php?id=528812561&stat=1&tout=10&osbt=2&osv=6.1&osbd=7600&ossp=0.0&ulv=2&elv=0&rad=0&agp=1&devicea=0&devicev=0&uname=phillip.price&cname=WIN-191HVE3KTLO&vpn=0&tvrv=0.2.2.2
Kevin Breen submitted his write up in which he said the answer was in the HTTP strings but within the process memory dump of the SkypeC2AutoUpdate.exe.
Time to fire up Vol and have a further look into SkypeC2AutoUpdate.exe.
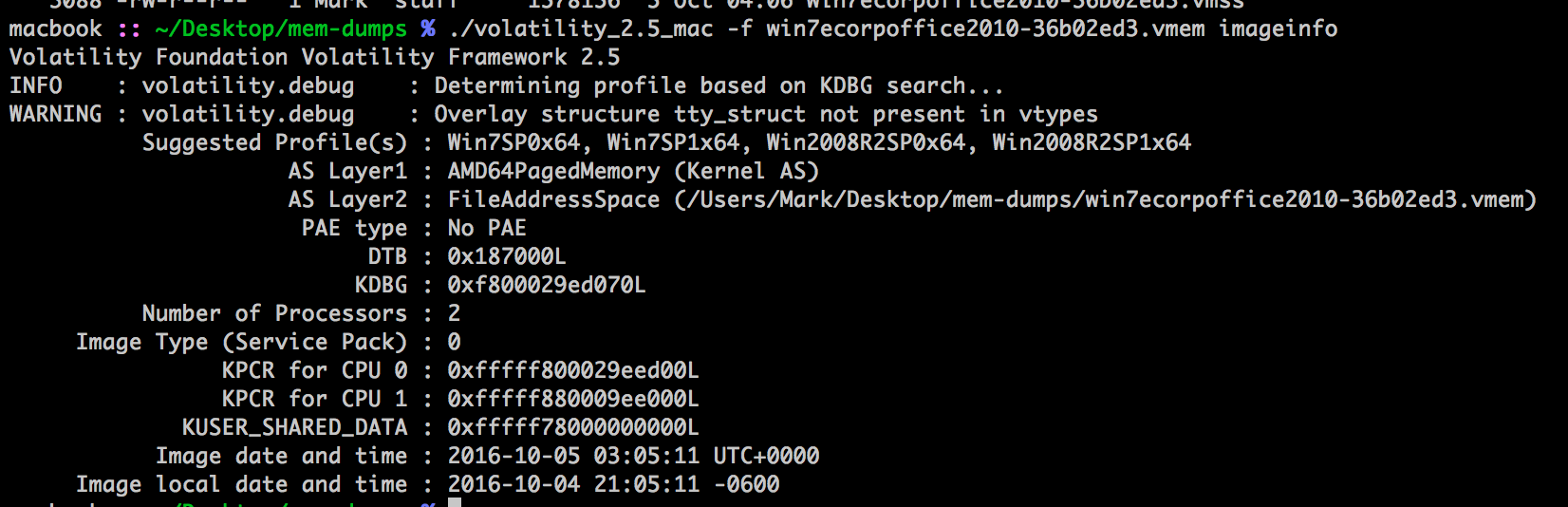
First thing is to get the image type of the memory dump.
./volatility_2.5_mac -f win7ecorpoffice2010-36b02ed3.vmem imageinfo
Now we can show the running processes.
./volatility_2.5_mac -f win7ecorpoffice2010-36b02ed3.vmem --profile=Win7SP1x64 pslist
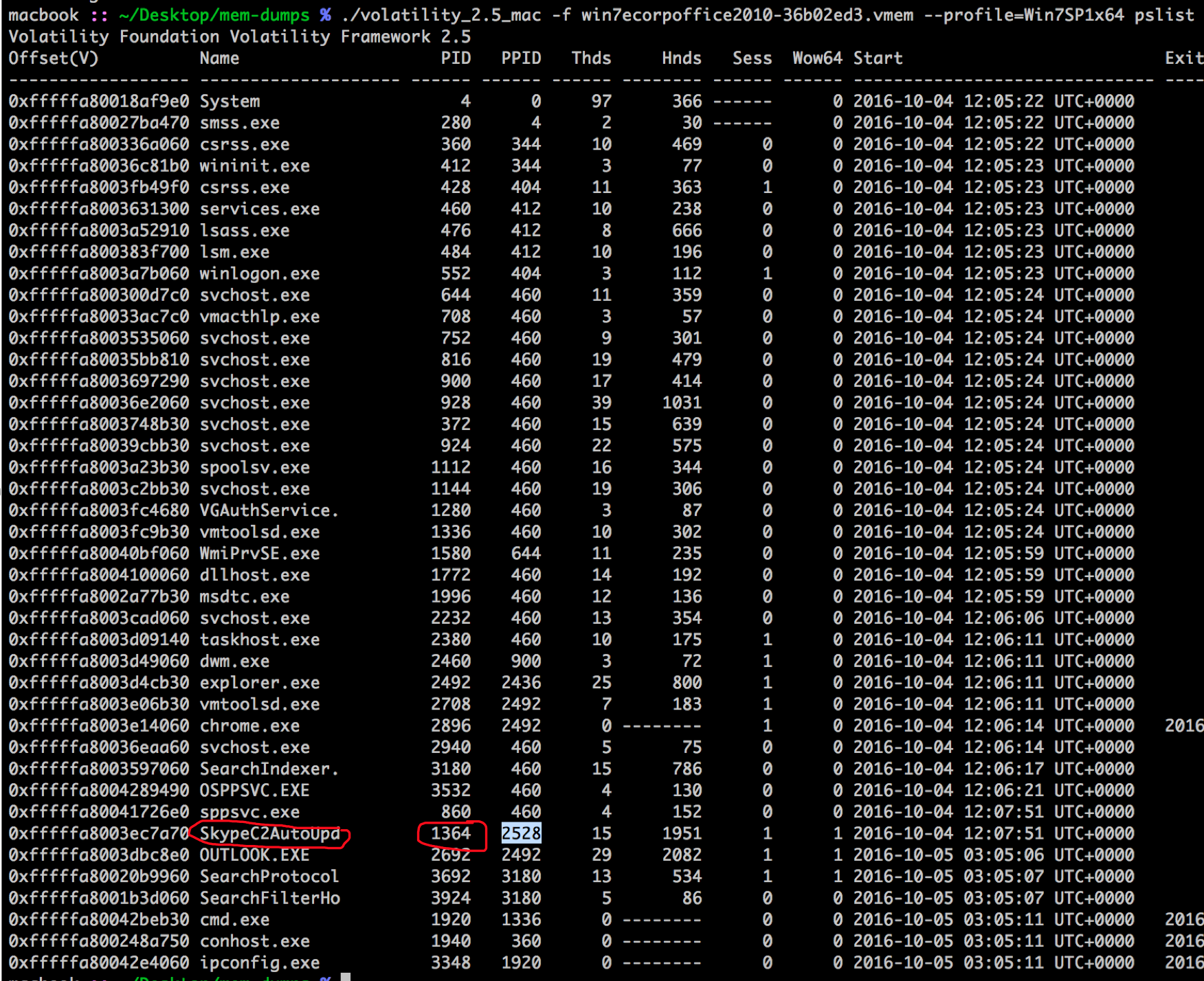
We can dump the process memory for that PID.
./volatility_2.5_mac -f win7ecorpoffice2010-36b02ed3.vmem --profile=Win7SP1x64 memdump -D ./evidence -p 1364
strings -n 10 1364.dmp | grep 54.174.131.235
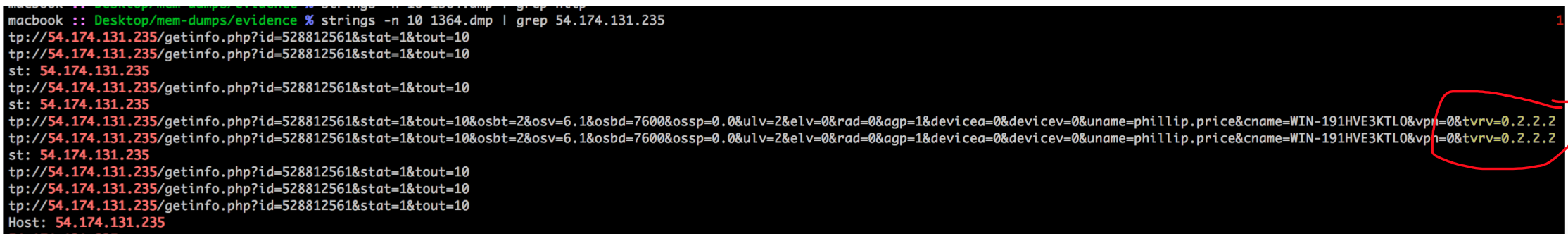
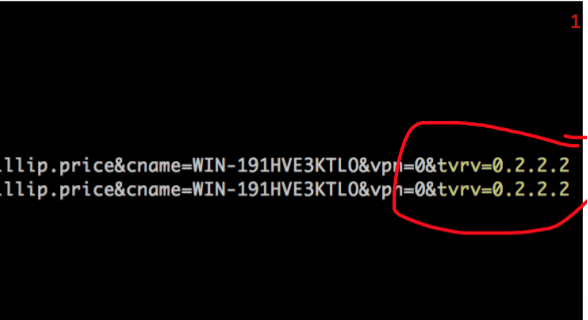
Answer: 0.2.2.2
Onto part 2...


