GrrCon 2017 DFIR write up - Level 1
#GrrCon 2017 #DFIR #CTF challenge. Several host images and memory dumps need to be analysed and investigated. Submit IOCs as you progress...

SPLOILER ALERT Some answers will be available - I'm currently still playing the later rounds, so some of this might seem unfinished. Hopefully this can help others get started.
Intro
This year's CTF is a realistic digital forensics and incident response challenge where you submit indicators of compromise as you go. It's also based on the characters from the Mr. Robot TV series so some names might be familiar.

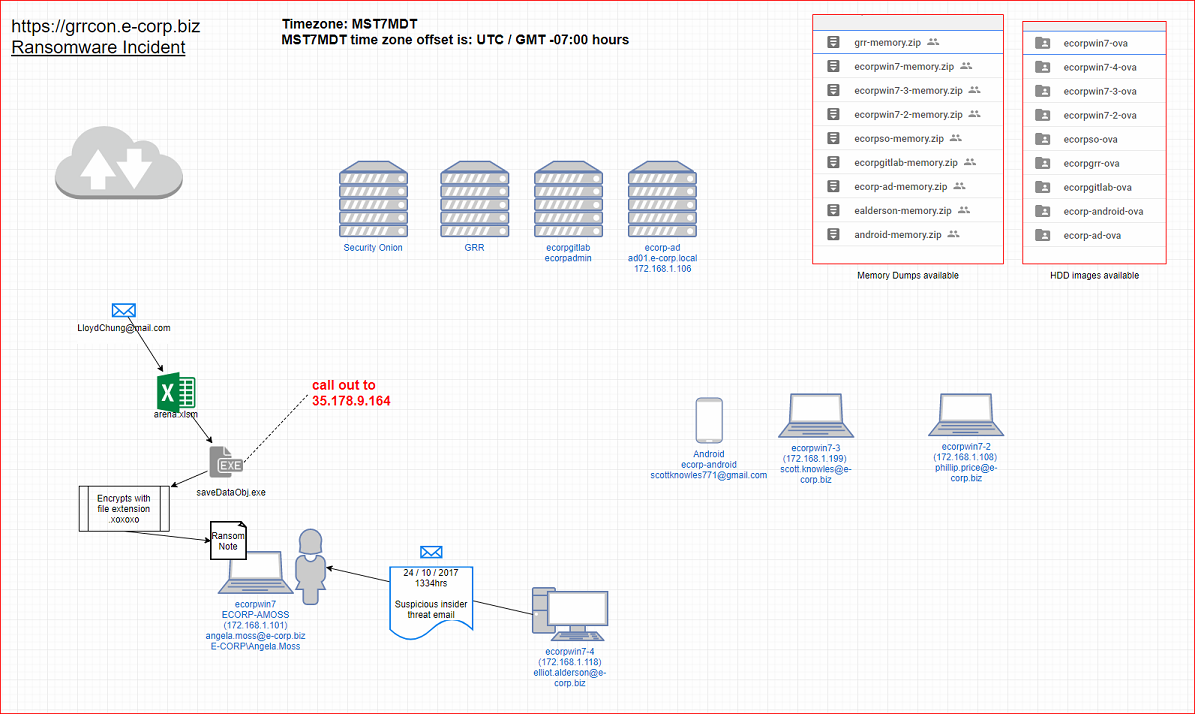
Download the network logs (NSM), memory images and disk images before proceeding. The ECORPSO provided image contains network logs + memory images for your ease.
Everything you need it over at https://grrcon.e-corp.biz and Level 1 can be started here https://grrcon.e-corp.biz/level1. Downloads https://grrcon.e-corp.biz/Downloads.
Computer ecorpwin7 is owned by Angela Moss and has recently been infected with what looks like ransomware. We have to investigate and submit indicators to score points.
Tools I used:
- SANS SIFT / Remnux / Kali / Windows sandpit VM (I used my own but these 90 eval VMs are perfect - just load your tools)
- Volatility Framework - standalone Mac and SIFT (comes with various +plugins).
- Timeline Explorer by Eric Zimmerman https://ericzimmerman.github.io/
- Draw.io / OneNote for note taking and diagramming.
Sandpit VM tools - I'm sure there are better lists but these are mine. Not all were used but most should help.
Another little tip is to use the free SANS resources especially the posters
https://www.sans.org/security-resources/posters/
Key ones;
- Finding Evil
- Windows Forensics Evidence Of
- SIFT & Remnux Poster
- DFIR Advanced Smartphone Forensics
1. Network Logs
Although we're looking at something that might have ran on Angela's PC I wanted to understand the network a bit more first. Plus I knew I had to do it at some stage as part of this 3 level CTF and it could possibly help.
I decided to attack these logs via the commandline and not use the Elastic Search / Security Onion provided VM. My SIEM skills are Splunk biased but I should really learn more about ELK in future! Given the amount of content in the CTF I'd rather crack on and revisit ELK stack after.
Just to note; not all network traffic will make much sense at this moment in time but look for anything abnormal and take note for later use.
Downloading and extracting the logs /nsm/bro/extracted/ is always a good place to start if available. Throw these extracted executables into VT to quickly check their malicious nature and work backwards from there.
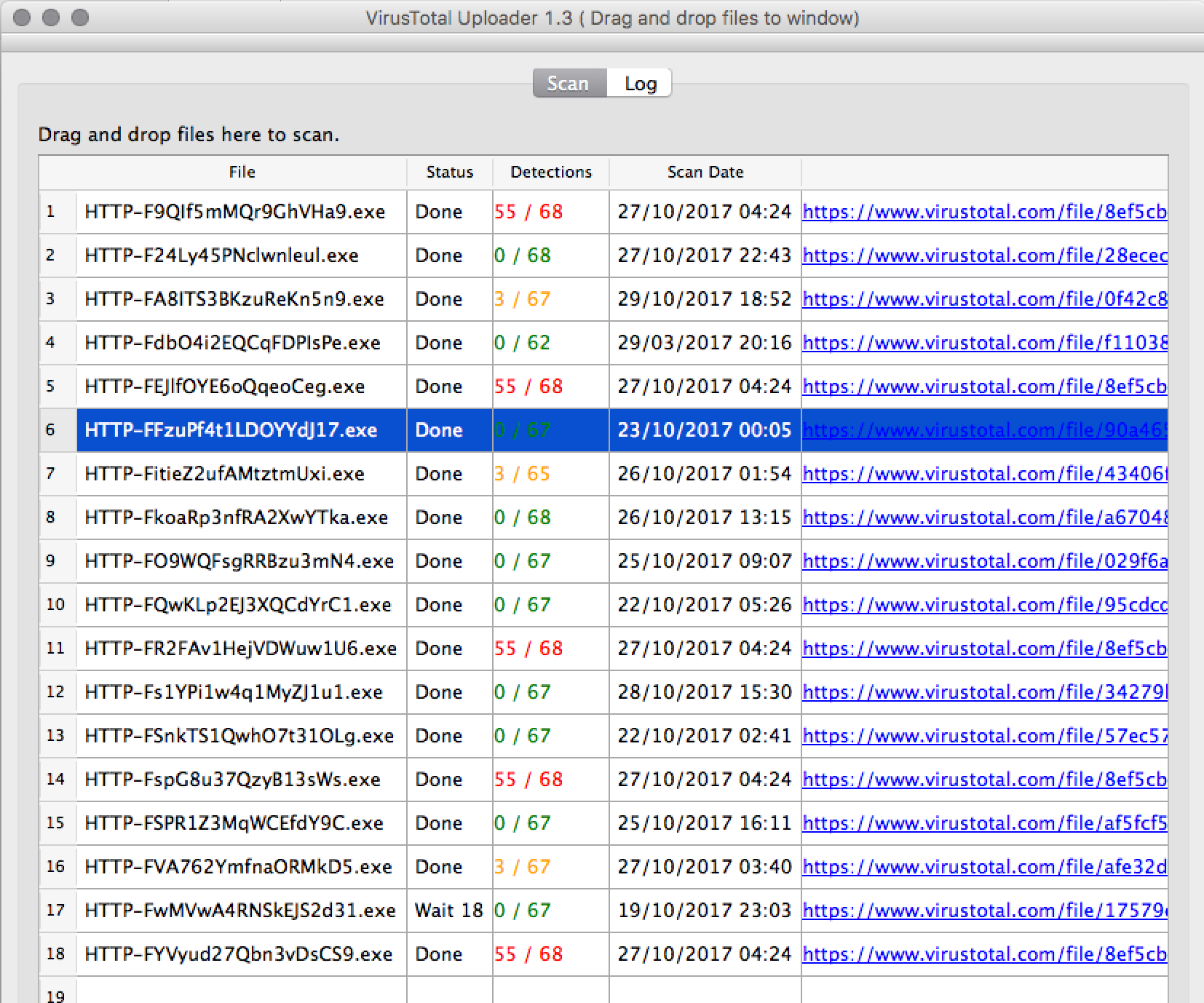
Submit MD5 hash 256d4639b4514c420f482cc9e795cac3
VirusTotal
Hydrid Analysis
Also, while moving data around my AV kicked off
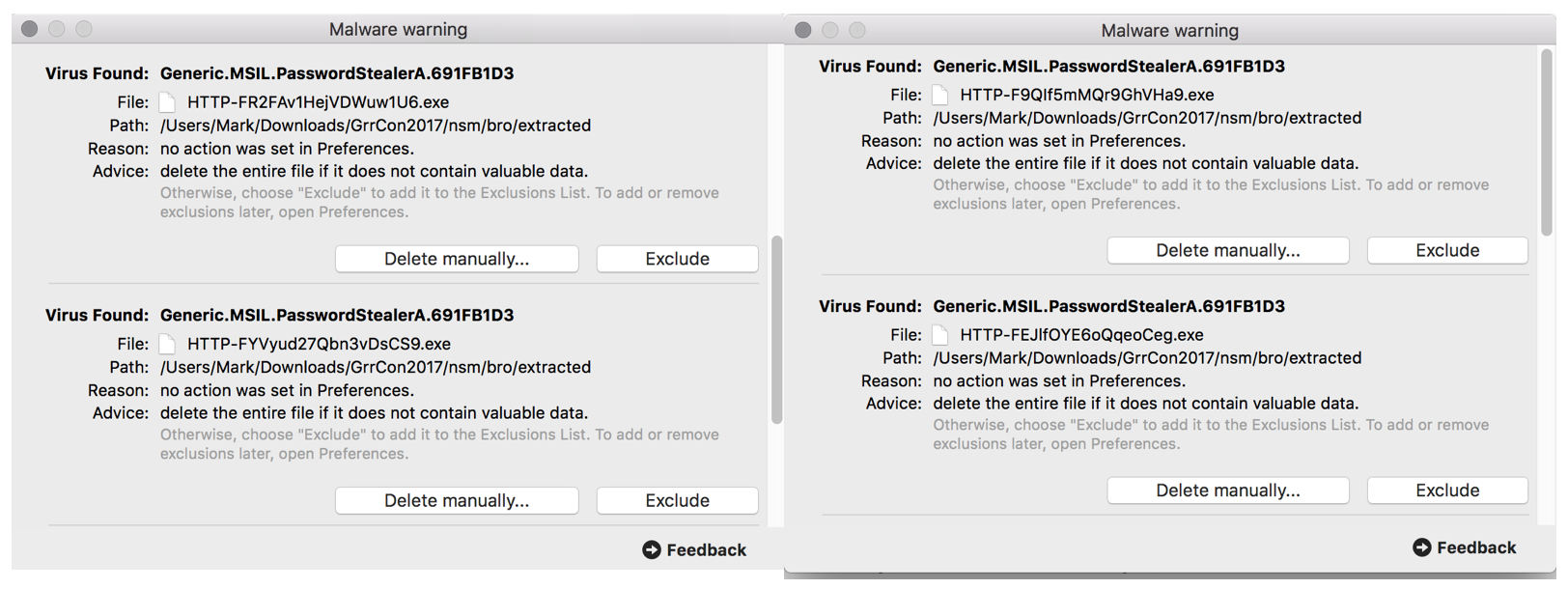
Try find where these executables came from
zcat < 2017-10-*/*http* | grep -v "windowsupdate" | grep exe
...
45.62.213.95 8080 11 GET win.budgetshowdown.com /psa.exe
45.62.213.95 8080 1 HEAD win.budgetshowdown.com /web/un.exe
45.62.213.95 8080 1 GET win.budgetshowdown.com /web/pputty.exe
...
Microsoft BITS/7.5
Submit USERAGENT Microsoft BITS/7.5
Submit DOMAIN budgetshowdown.com
zcat < 2017-10-*/*http* | grep -v "windowsupdate" | grep 45.62.213.95
...
45.62.213.95 8080 1 HEAD win.budgetshowdown.com /web/Tools.zip
45.62.213.95 8080 1 HEAD win.budgetshowdown.com /web/tools2.zip
45.62.213.95 8080 1 HEAD win.budgetshowdown.com /web/m.zip
...
zcat < 2017-10-*/*http* | grep -v "windowsupdate" | grep -v 172.168.2.102
172.168.1.108 62647 45.62.213.95 8080 8 GET win.budgetshowdown.com /a.cab
zcat < http_eth1.* | grep 172.168.1.120 | more
172.168.1.120 45051 172.217.12.14 80 1 GET goo.gl /vvsfmp - 1.1 Wget
172.168.1.120 45638 210.240.39.201 80 1 GET git.linux.org.tw /houdini4_32.tgz - 1.0 Wget
172.168.1.120 55965 172.217.12.3 80 1 GET www.gstatic.com /android/config_update/07252017-sms-blacklist.metadata.txt - 1.1 AndroidDownloadManager/4.4.4 (Linux; U; Android 4.4.4; VMware Virtual Platform Build/KTU84Q)
172.168.1.120 45053 172.217.12.14 80 1 GET goo.gl /IP06KC - 1.1 Wget
172.168.1.120 37169 212.122.81.210 80 1 GET dl.android-x86.org /houdini.php?v=4_32 - 1.1 Wget
172.168.1.120 55965 172.217.12.3 80 2 GET www.gstatic.com /android/config_update/07252017-sms-blacklist.txt - 1.1 AndroidDownloadManager/4.4.4 (Linux; U; Android 4.4.4; VMware Virtual Platform Build/KTU84Q)
172.168.1.120 40617 78.62.182.74 80 1 GET zebra-mirror.ddscentral.org /dl.android-x86.org/houdini/4_32/houdini.tgz - 1.1 Wget
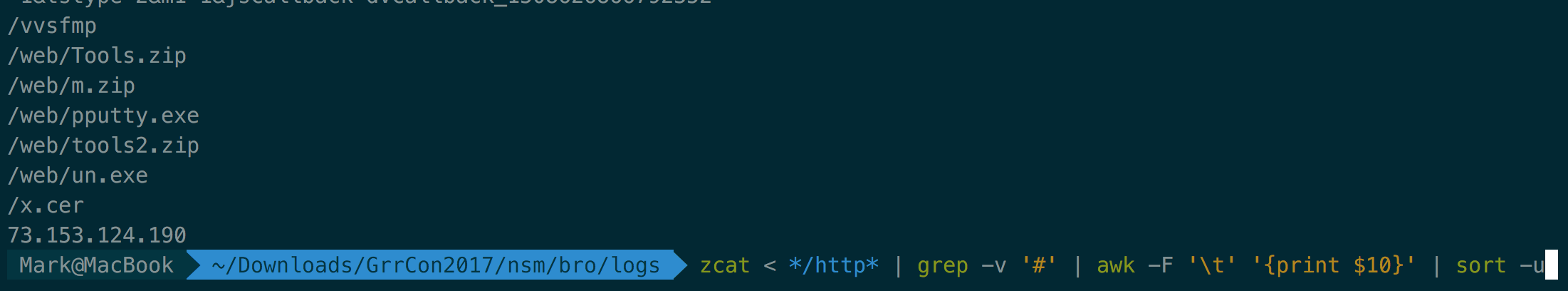
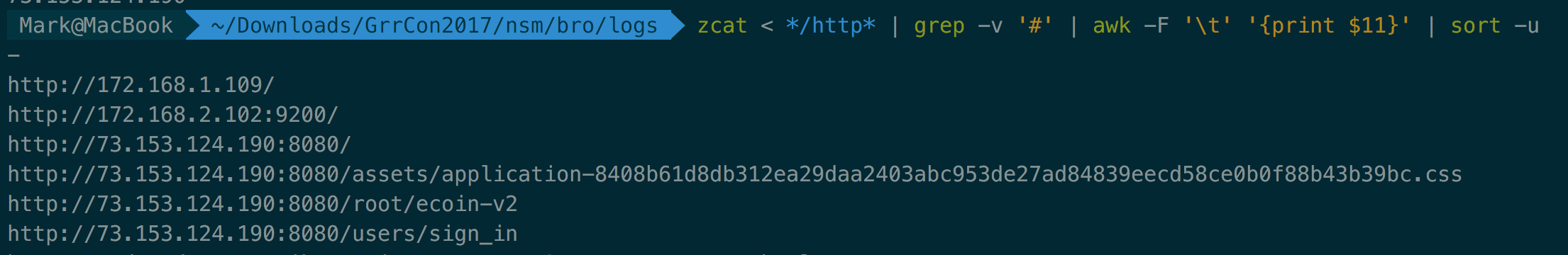
zcat < */http* | grep -v '#' | awk -F '\t' '{print $10}' | sort -u
...
/vvsfmp
/web/Tools.zip
/web/m.zip
/web/pputty.exe
/web/tools2.zip
/web/un.exe
/x.cer
73.153.124.190
/psa.exe
/redir/allservices/?sv=5&version=12.0.7601.17514&locale=409&userlocale=409&geoid=f4&parch=x64&arch=x86
/root/ecoin-v2
/root/ecoin-v2/blob/master/README.md?format=json&viewer=rich
/root/ecoin-v2/refs/master/logs_tree/?_=1508898572188
/root/ecoin-v2/repository/archive.tar.bz2?ref=master
/rootr1/MEwwSjBIMEYwRDAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6+MgGqMQQUYHtmGkUNl8qJUC99BM00qP/8/UsCCwQAAAAAAURO8DYx
/roots/dstrootcax3.p7c
...
zcat < */http* | grep -v '#' | awk -F '\t' '{print $13}' | sort -u
2.Memory Analysis of ecorp7win
The memory capture file: ecorp7win-mem
Check the profile and do quick triage for anything abnormal. Not much running here besides Outlook and the elastic host agent.
vol.py imageinfo -f ecorpwin7-2a617fe4.vmem
vol.py -f ecorpwin7-2a617fe4.vmem --profile=Win7SP1x64 pstree
vol.py -f ecorpwin7-2a617fe4.vmem --profile=Win7SP1x64 netscan
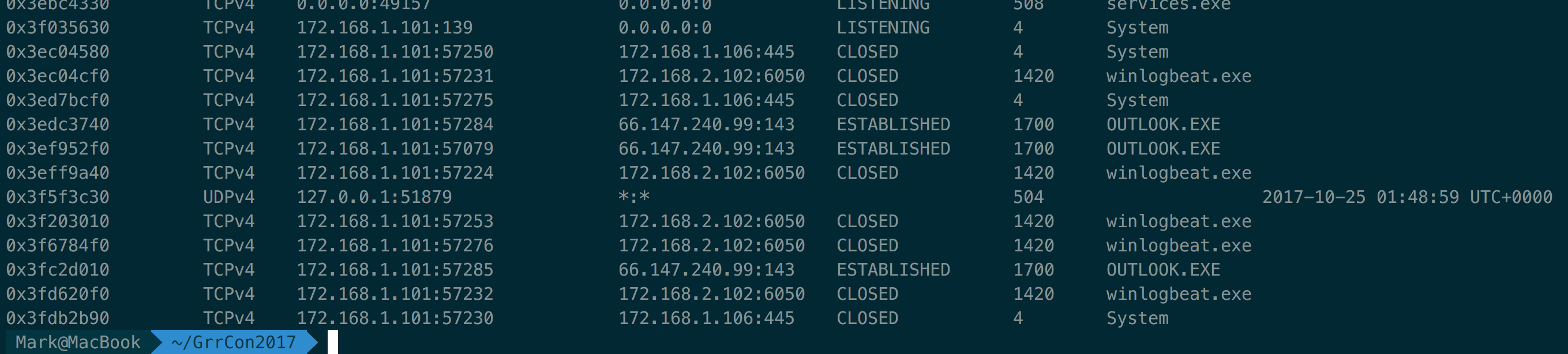
Note the IP of her machine ecorp7win-mem (172.168.1.101). Next I recently found this super useful for painting a picture of what the user saw. This was the last thing on the desktop at the time of the memory capture.
vol.py -f ecorpwin7-2a617fe4.vmem --profile=Win7SP1x64 screenshot --dump-dir=/
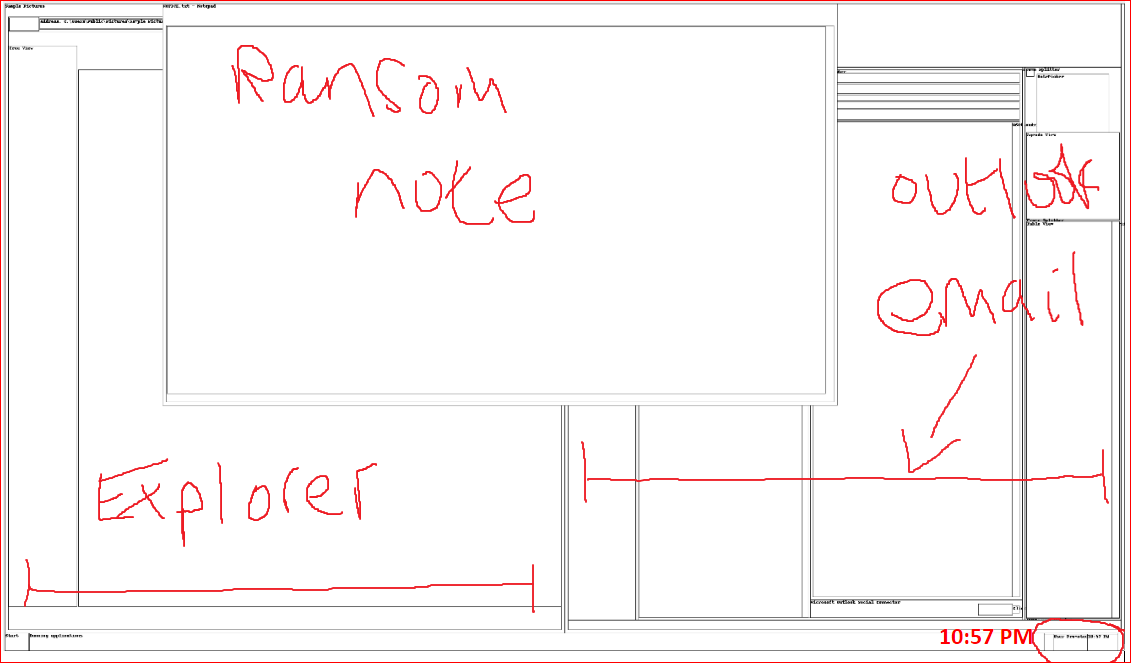
Windows Explorer and Outlook are open with the ransom note on her PC. Time is ~10:57PM. I guess they clicked an email which lead to code execution displaying the note. Capture what is on the Notepad for confirmation.
vol.py -f ecorpwin7-2a617fe4.vmem --profile=Win7SP1x64 editbox
will show the contents of NOTICE.txt.
vol.py -f ecorpwin7-2a617fe4.vmem --profile=Win7SP1x64 pslist
vol.py -f ecorpwin7-2a617fe4.vmem --profile=Win7SP1x64 pstree
vol.py -f ecorpwin7-2a617fe4.vmem --profile=Win7SP1x64 psaux
Dump the memory for the running processes OUTLOOK.exe
vol.py -f ecorpwin7-2a617fe4.vmem --profile=Win7SP1x64 memdump -p 1700 -dump-dir=/cases/mem-dump/
vol.py -f ecorpwin7-2a617fe4.vmem --profile=Win7SP1x64 memdump -p 1728 -dump-dir=/cases/mem-dump/
See remenance of emails in memory using strings on the dumped data or use
vol.py -f ecorpwin7-2a617fe4.vmem --profile=Win7SP1x64 yarascan -Y "From:"
Return-Path: <[email protected]>
Delivered-To: [email protected]
Received: from host299.hostmonster.com
by host299.hostmonster.com (Dovecot) with LMTP id odbgJUPk71lmdAAAeAlg1Q
for <[email protected]>; Tue, 24 Oct 2017 19:09:23 -0600
Return-path: <[email protected]>
Envelope-to: [email protected]
Delivery-date: Tue, 24 Oct 2017 19:09:23 -0600
Received: from mout.gmx.com ([74.208.4.201]:61248)
by host299.hostmonster.com with esmtps (TLSv1.2:ECDHE-RSA-AES128-GCM-SHA256:128)
(Exim 4.87)
(envelope-from <[email protected]>)
id 1e7ACA-00088w-RB
for [email protected]; Tue, 24 Oct 2017 19:09:23 -0600
Received: from [71.195.27.15] by 3c-app-mailcom-lxa15.server.lan (via HTTP);
Wed, 25 Oct 2017 03:09:11 +0200
MIME-Version: 1.0
Message-ID: <trinity-032d6e70-6bf8-440d-ad84-acb728d53f03-1508893750403@3c-app-mailcom-lxa15>
From: "Lloyd Chung" <[email protected]>
To: [email protected]
Subject: Cool game
Content-Type: multipart/mixed;
boundary=rehcsed-98679392-c2a7-4941-878c-f44589394aab
Date: Wed, 25 Oct 2017 03:09:11 +0200
Importance: normal
Sensitivity: Normal
X-Priority: 3
From: <[email protected]>
To: <[email protected]>
Subject: help this game lloyd sent me is bugging out
Date: Tue, 24 Oct 2017 19:58:09 -0600
Message-ID: <[email protected]>
MIME-Version: 1.0
Content-Type: multipart/mixed;
boundary="----=_NextPart_000_0007_01D34D02.6AEEBAE0"
X-Mailer: Microsoft Outlook 14.0
Thread-Index: AQMqpZDQ6p+OA+881tRTSsrOPslmmg==
Content-Language: en-us
X-OlkEid: 498403204A4FFABCBBD1A64FB3EB961FA476515A
This is a multipart message in MIME format.
------=_NextPart_000_0007_01D34D02.6AEEBAE0
Content-Type: multipart/alternative;
boundary="----=_NextPart_001_0008_01D34D02.6AEEBAE0"
------=_NextPart_001_0008_01D34D02.6AEEBAE0
Content-Type: text/plain;
charset="us-ascii"
Content-Transfer-Encoding: 7bit
I think this game I wanted to pass the time is messed up I got this
--
Quick search for PST files from memory.
vol.py -f ecorpwin7-2a617fe4.vmem --profile=Win7SP1x64 filescan | grep pst
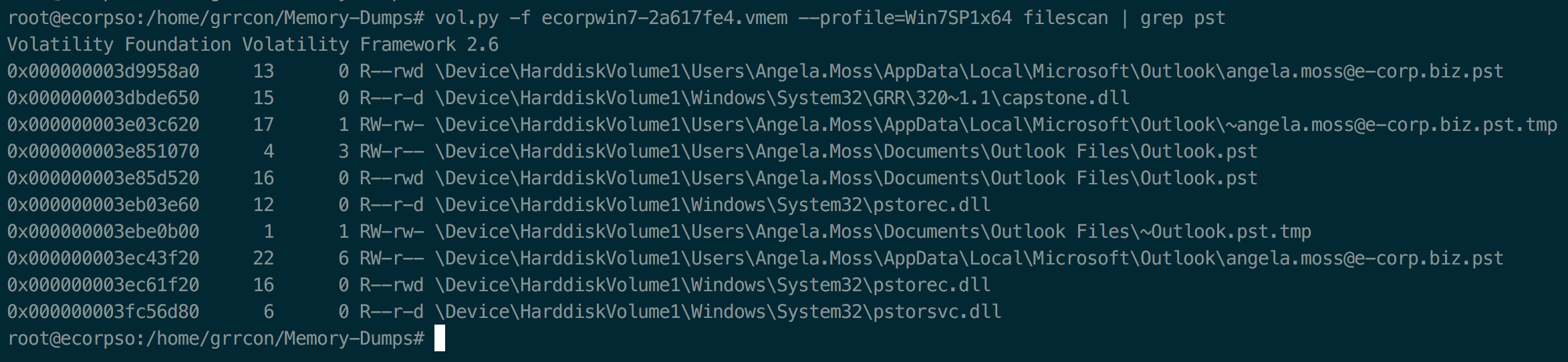
Probably best to take note for now and pull from disk image later as it'll be much more easier.
Another quick win is to filscan for .exes in memory.
vol.py -f ecorpwin7-2a617fe4.vmem --profile=Win7SP1x64 filescan > ecorpwin7_fiolescan_output.txt
cat ecorpwin7_filescan_output.txt | grep.exe
cat ecorpwin7_filescan_output.txt | grep.exe | grep -v Windows
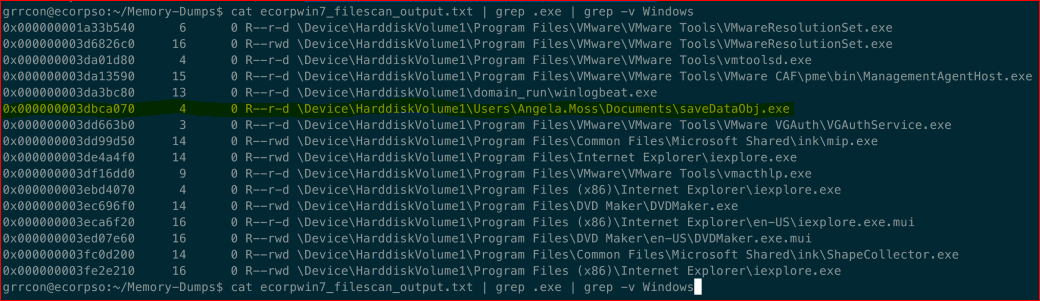
SaveDataObj.exe is suspicious. Noted for later. We can recover the file from memory but as we have the disk image we can check there first. If it was deleted and we could not undelete then carving it from memory would be an option.
3.Disk Analysis of ecorp7win
There are various ways to mount a VMDK disk and extract the contents. I'm using a Mac so methods will differ. I used Paragon VMDK Mounter to quickly triage but found the below worked well too.
- Import downloaded OVA disk image.
- Once VM is imported. Ignore any OVA warning / error messages. Click retry.
- Under MacOS Vmware, Right click > Open "Show Package Contents"
- Remove VMDK and attach to SIFT Workstation VM (while SIFT vm is powered off)
a. Add disk
b. Existing
c. Share with VM - Boot SIFT
- Elevate to root
sudo su - - List disks/partitions
fdisk -l. Look for /dev/sdXX or similar at the bottom mount -t ntfs -o ro /dev/sdc1 /mnt/windows_mount/- Browse to
/mnt/windows_mount/to view files. - Done
To quickly triage known badness I kick off a Loki yara scan of the disk.
git clone https://github.com/Neo23x0/Loki.git
cd Loki
sudo apt-get install python-pip
pip install netaddr psutil pylzma yara-python
python loki.py -p /mnt/windows_mount/ sansforensics@siftworkstation:~/Loki$ sudo python loki.py -p /mnt/windows_mount
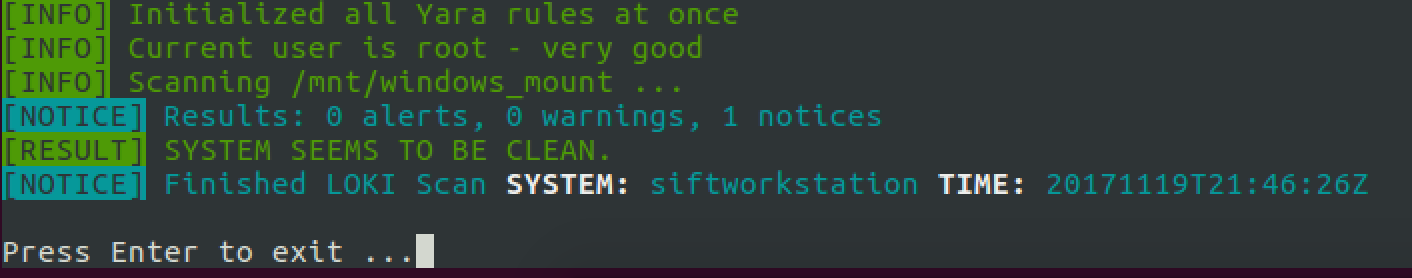
Nothing found so I proceeded to search for the PST files from the disk as indicated in the earlier memory analysis. Once found in C:\Users\Angela.Moss\AppData\Local\Microsoft\Outlook\ copy locally and fire up KernelPSTviewer
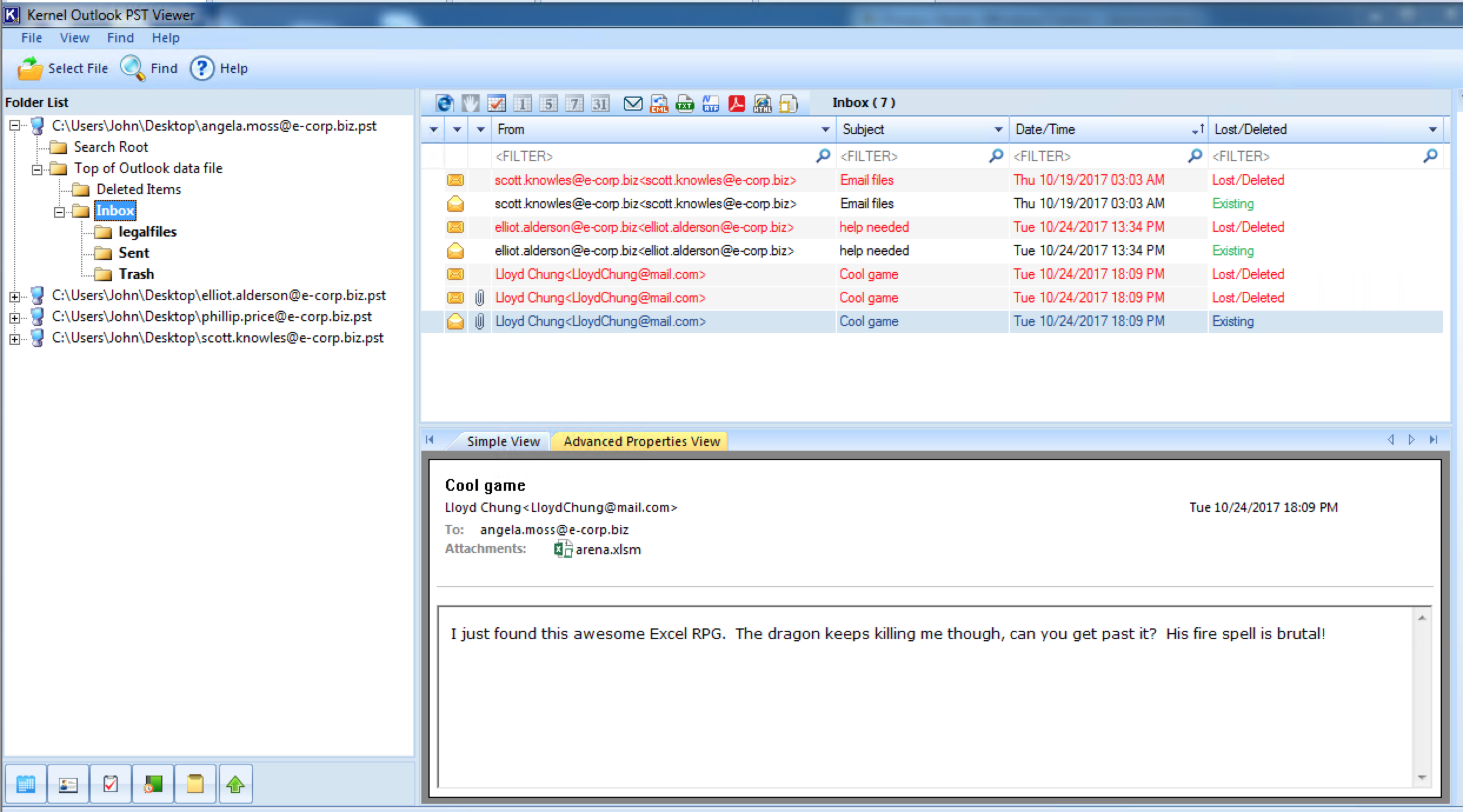
There are lots of emails to take note of here. I read them all and added them to a timeline order. Interesting stuff...
arena.xlsm
Submit MD5 1ae87e7366afaf3758c51621ab598915
saveDataObj.exe
Submit MD5 683183673f340364a170db3382248ab9
Submit EMAIL [email protected]
Quick analysis of the binary.
strings saveDataObj.exe | grep -oE "\b\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}\b"
Submit IP 35.178.9.164
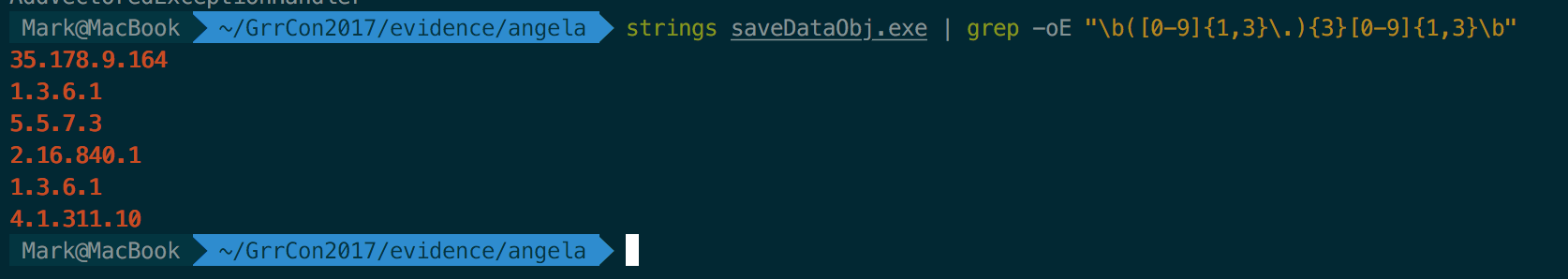
Check NSM logs for that IP - doesn't seem to be reaching out.
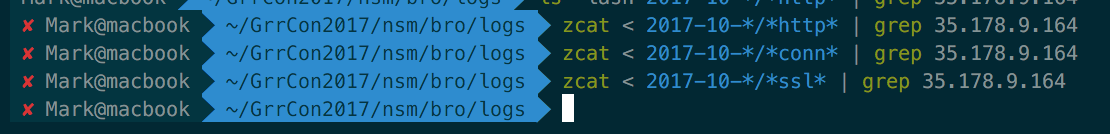
As caught in the memory forensics earlier, run a system wide search on the disk for SaveDataObj.exe to see where it copied itself.
find -type f -name saveDataObj.exe -exec md5sum {} \;
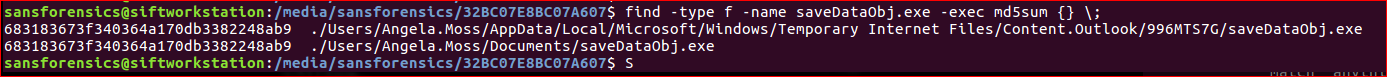
So manually checking over Document locations. Possibly encrypted files?
C:\Users\All Users\Documents\My Pictures\Sample Pictures\
using file you can check the file headers against a known list. I would normally expected picture formats not data. Content is scrambled when view with cat too.
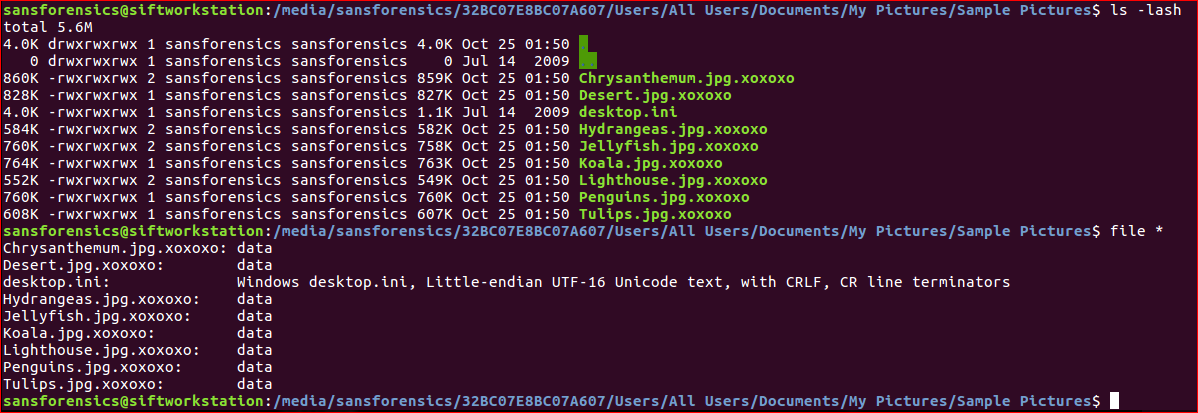
Odd location to encrypt. So will check using the extension for any other places.
find -type f -name *.xoxoxo
find -type f -name *.xoxoxo | wc -l
So just a few more files (1831)... looks like the ransomware has a specific file type to encrypt. Not a complete match with the NOTICE.txt quote of
We're sorry but 4,569 of your important documents have been encrypted! You must pay us 10.000 Monero to be given the key to get your information back.
Browse to https://github.com/WaY5x3FIEJ1lvkFt7m5s/dec for instructions on how to proceed.
Your personal key is 8ibuPEJyxO52JCflG3lJo_WQX2Wp0BGJi2HzuVMYa6EuAyHtqcfyGYV6xBA9So5q
Also of note, which leads onto Level 2's Insider Threat theme if you've already view the question.
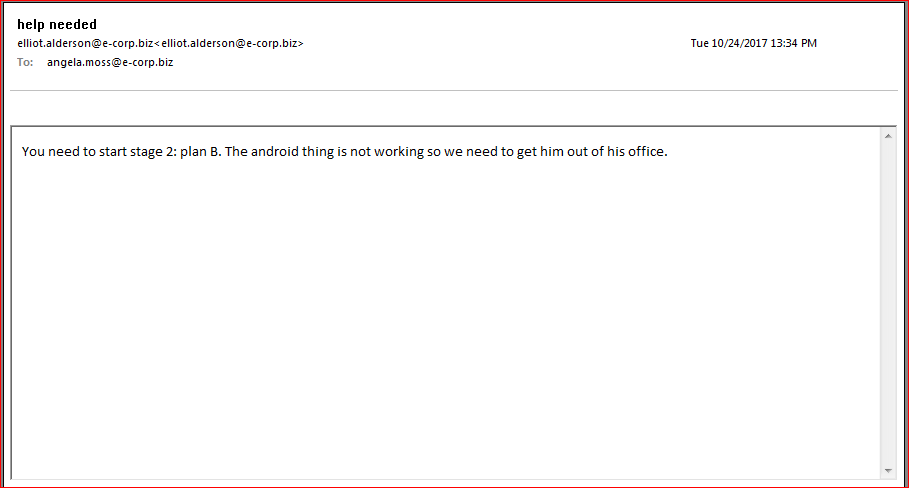
I noticed in some of the results I'm getting that the time is skewed so we need to confirm the correct timezone. The above email has had the time changed locally on my sandpit Windows 7 VM but when viewing the PST at first you will get the early hours if working from UTC/GMT/BST.
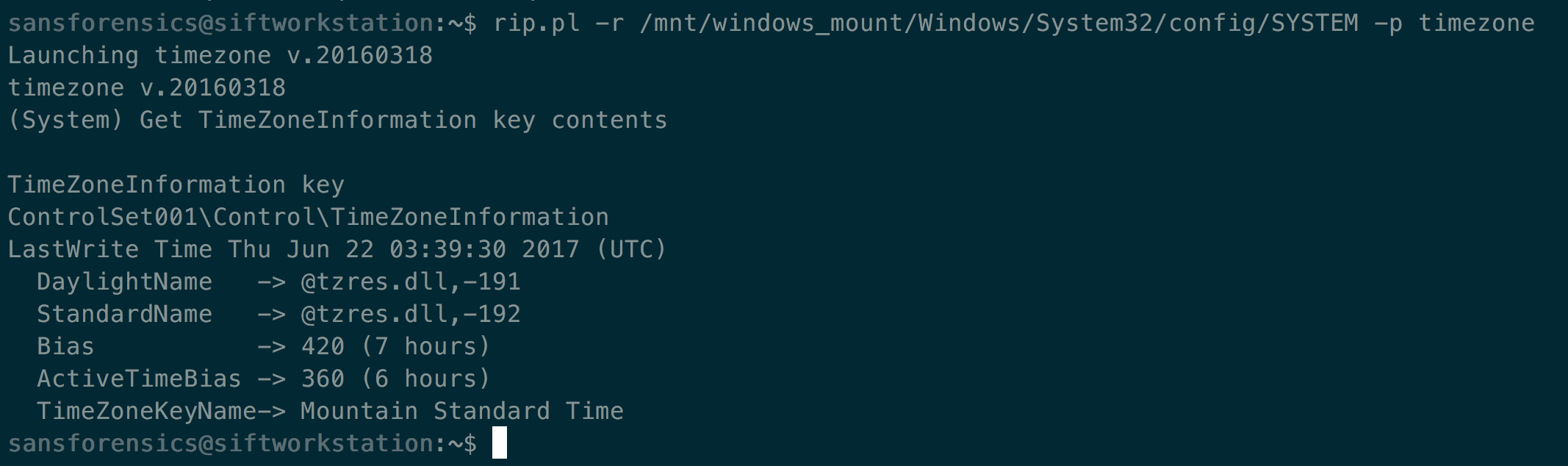
rip.pl -r /mnt/windows_mount/Windows/Sytem32/config/SYSTEM -p timezone
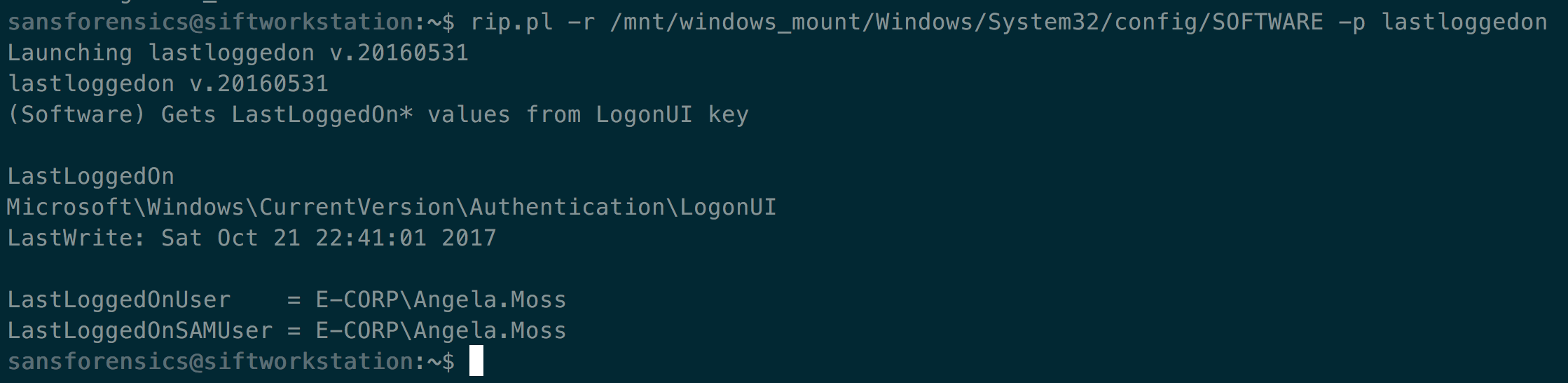
Just confirm the last logged on user was Angela.
rip.pl -r /mnt/windows_mount/Windows/Sytem32/config/SOFTWARE -p lastloggedon
4. TIMELINING
Unlike previous GrrCon CTFs we have lots more information and on several systems. Using timelining like log2timeline and Volatility's timeliner tools it'll help automate and visualize events that have occurred. Rinse repeat with the other host images too.
MEMORY TIMELINE
vol.py -f ecorpwin7-2a617fe4.vmem --profile=Win7SP1x64 timeliner --tz=MST7MDT --output=body --output-file=volmem-body_v2
mactime -b memory-body -z MST7MDT -d > memory-timeline_MST7MDT.csv
DISK TIMELINE
log2timeline.py /cases/plaso.dump /mnt/windows_mount/
pinfo.py -v /cases/plaso.dump
psort.py -z list
psort.py -z "US/Mountain" -o L2tcsv /cases/plaso.dump "date > '2017-10-25' AND date < '2017-10-26'" > /cases/supertimeline_MTZ.csv
SUPERTIMELINE
Combine those memory and disk timelines together.
log2timeline.py /cases/plaso.dump /mnt/windows_mount/
pinfo.py --verbose /cases/plaso.dump
Check configured_zone = MST7MDT. PINFO will list out some more useful information that you can take note of such as Host, Time Zone, User information, and OS versions.
vol.py -f ecorpwin7-2a617fe4.vmem --profile=Win7SP1x64 timeliner --tz=MST7MDT --output=body --output-file=/cases/timeliner.body
log2timeline.py -z list
log2timeline.py --parsers "mactime" -z "US/Mountain" /cases/plaso.dump /cases/timeliner.body
psort.py -z "US/Mountain" -o L2tcsv /cases/plaso.dump "date > '2017-10-24' AND date < '2017-10-26'" > /cases/supertimeline_MST7MDT.csv
- Import
*.csvinto Time Line Explorer. - Filter on 24th October
- Run through it once and "tag" interesting or suspicious events.
- Filter on only tagged documents to build.
- Done
Generated, imported and filtered timeline in Time Line Explorer.
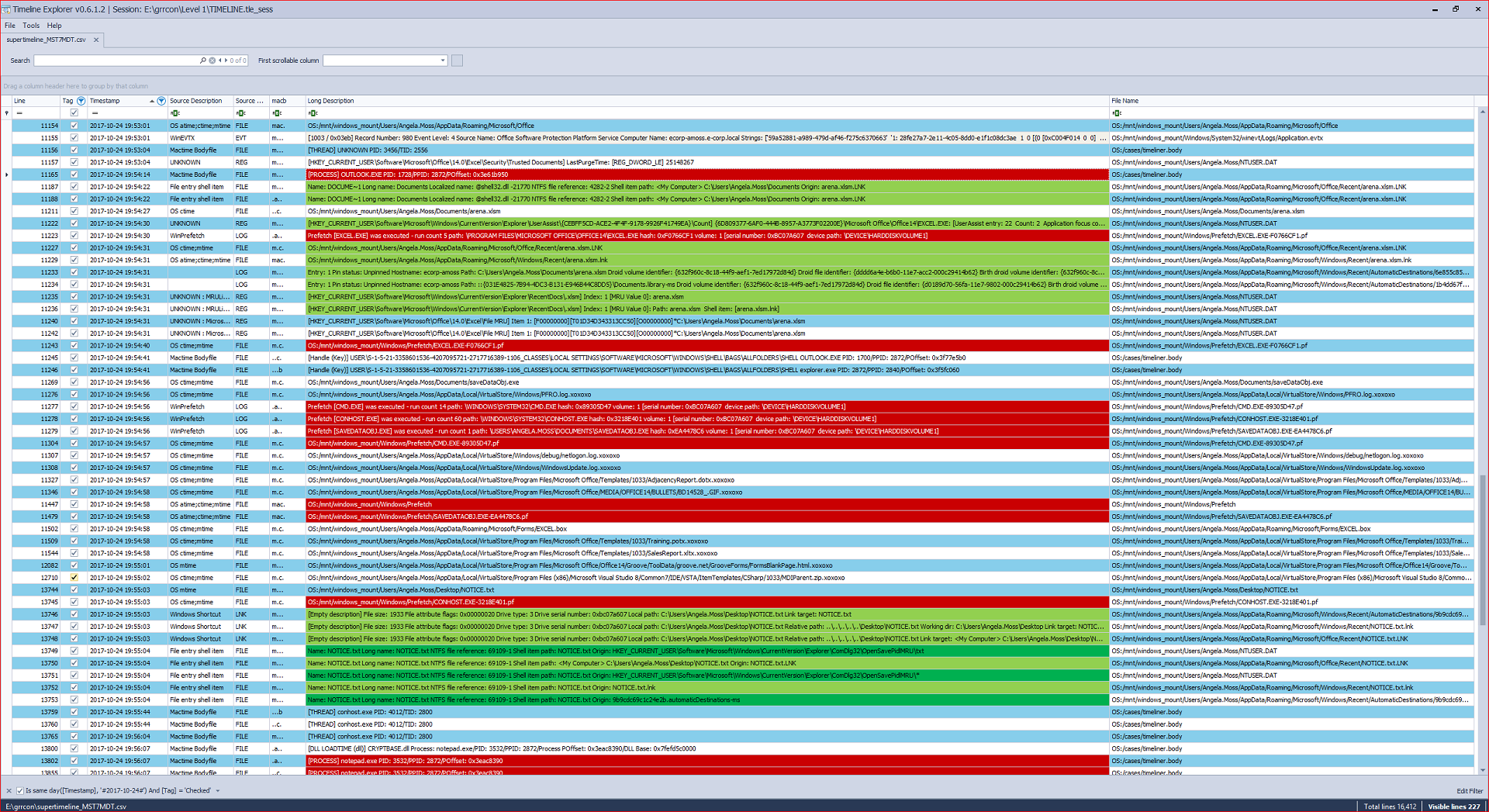
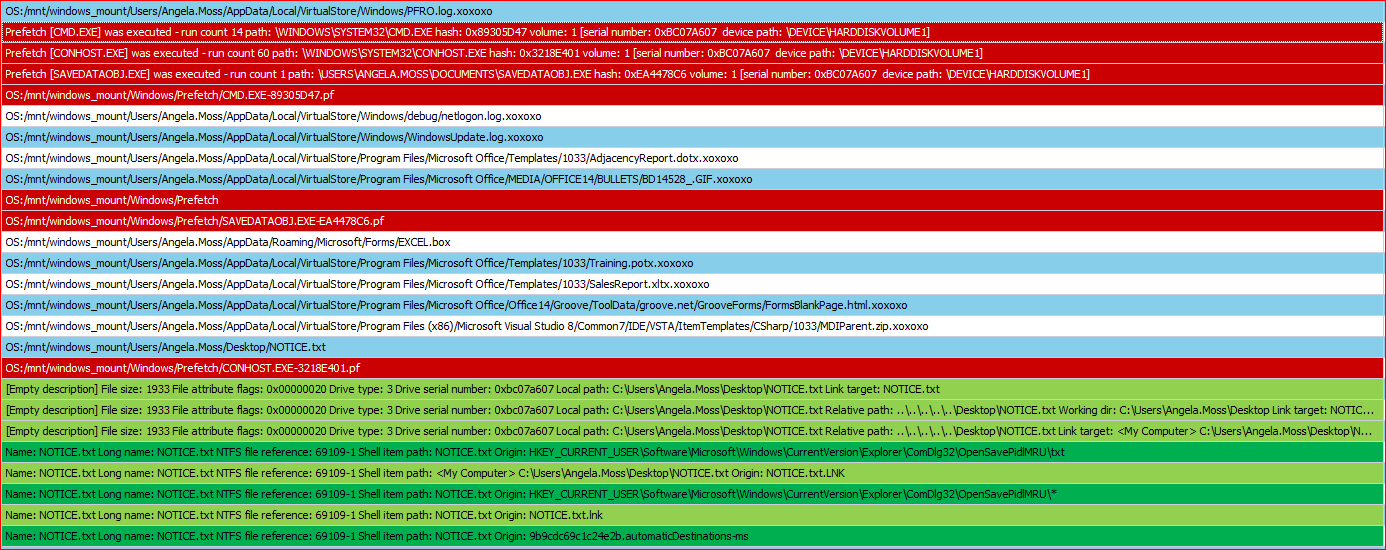
Opening Outlook, clicking the Excel attachment and SaveDataObj.exe hitting the disk.

Then is executed, starts encrypting lots files with extension .xoxoxo ....
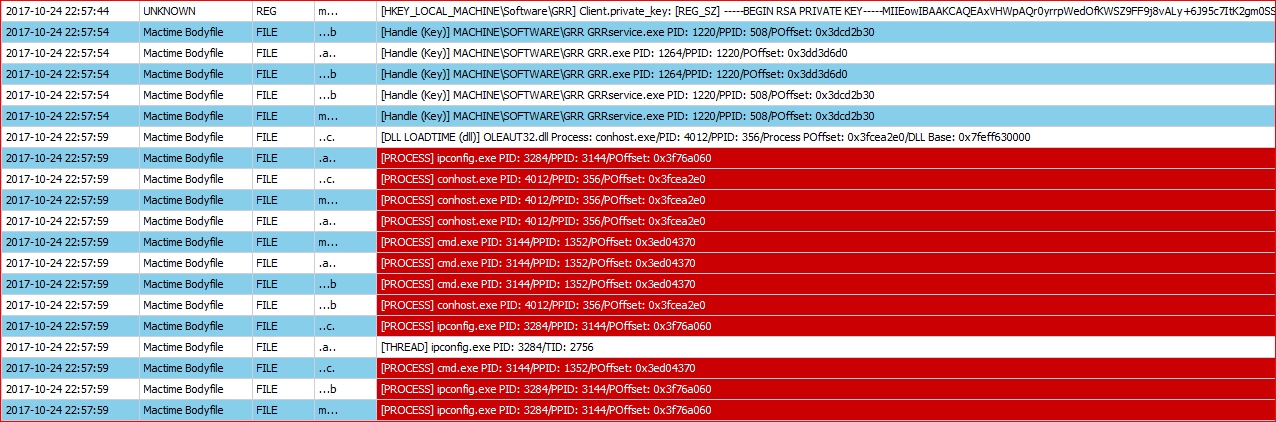
GRR ( Google Rapid Response ) kicking in @ 2257hrs like what we saw earlier in the ghost screenshot.
5. Diagramming (optional)
Not fully finished but it helped with getting the numerous systems painted out. As I go through the dumps I add key information such as login IDs, computer names, IPs, key files downloaded, malware execution etc.. hopefully by the end it should explain what happened. Take a look over at @malwareunicorn and her mad diagramming skills http://amanda.secured.org/zepto-ransomware-diagram-how-to/ (Check out Bad Rabbit and Wannacry diagrams). It would be awesome to be able to do this more fluidly during incidents...