Blue Team Basics - PCAP File Extraction
A few methods of how to carve data out of PCAPs. Whether this be a single analysis of some network traffic or part of a malware analysis lab.
Using Wireshark
Ideal for investigating smaller PCAPs but you tend to see a performance slip off after anything over 800MB.
- Run Wireshark / start capturing traffic and minimize.
- Browse to http://www.eicar.org/85-0-Download.html
- Download the HTTP eicar zip file.
- Stop Wireshark after the download has completed.
- Filter by 'http' using the BPF format in Wireshark's display filter bar.
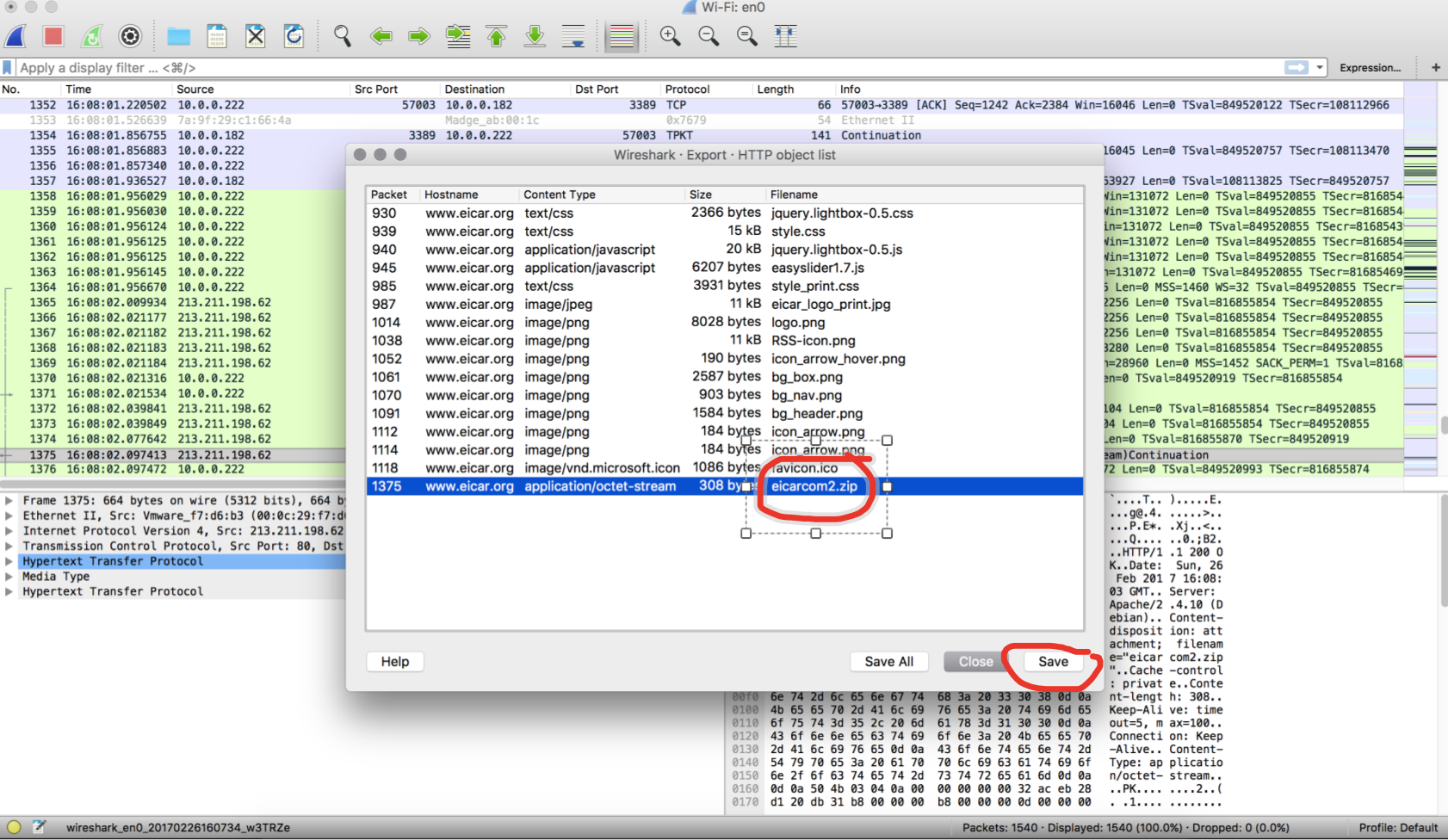
- Then to extract HTTP objects. [File > Export Objects > HTTP].
- Highlight the eicar file and save.
- Save the Wireshark capture. [File > Save As > test_eicar.pcap]
Using Bro IDS
A bit more advanced. I found this works very well when investigating larger PCAPs in your environment and can be easily automated. This can be used both OFFLINE 'PCAPS' and ONLINE 'live traffic'.
1.) Install Bro IDS (defaults) [/usr/local/bro]
You could use a Docker instance to get yourself set up ASAP https://github.com/blacktop/docker-bro but the extraction script isn't ready just yet in this release. One to watch.
2.) Enable the 'extract all' script in local.bro [/usr/local/bro/share/bro/local.bro]
@load frameworks/files/extract-all-files
3.) Set new extract default limit in local.bro. Defaults are 25Mb.
For this example the contents we are after are small, its best to be aware of the limits and to set them higher. For a production system you should be careful retaining this much data without consideration of maintenance and clear-down scripts.
[/usr/local/bro/share/bro/local.bro]
redef FileExtract::default_limit = 1000000000;
1000000000 = 1 GByte
4.) Then make sure you deploy the config locally to the single Bro instance.
broctl deploy
5.) Pass the PCAP to Bro to analyse. Run in the directory you wish to extract data to.
bro -Cr test_eicar.pcap local.bro "Site::local_nets += { 10.0.0.0/24 }"
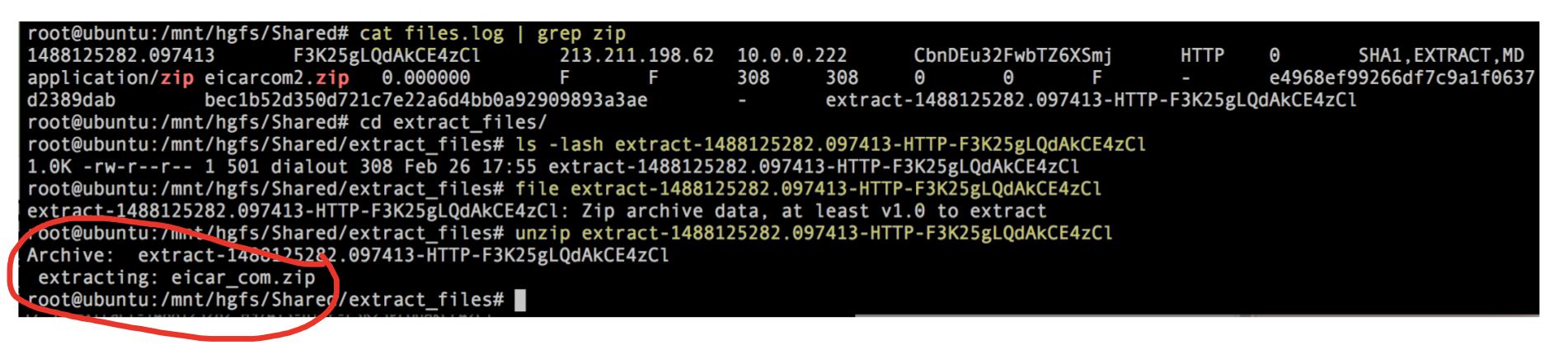
View [files.log] to determine which file is the eicar one, take the unique extraction file name and then extract as below.
Bro extraction limits: https://www.bro.org/sphinx/scripts/base/files/extract/main.bro.html
Using the cloud
A new trend to come out of the community only recently. Pretty certain they'll be using BRo in the backend with added pretty graphs / timelines / charts etc...

CAREFUL CONSIDERATION is needed when using these services. Before you start analyzing packet captures it is important to remember that once analysis has started the information within the packet capture file becomes available to the Internet.
Below. Example of PacketTotal's file extraction.
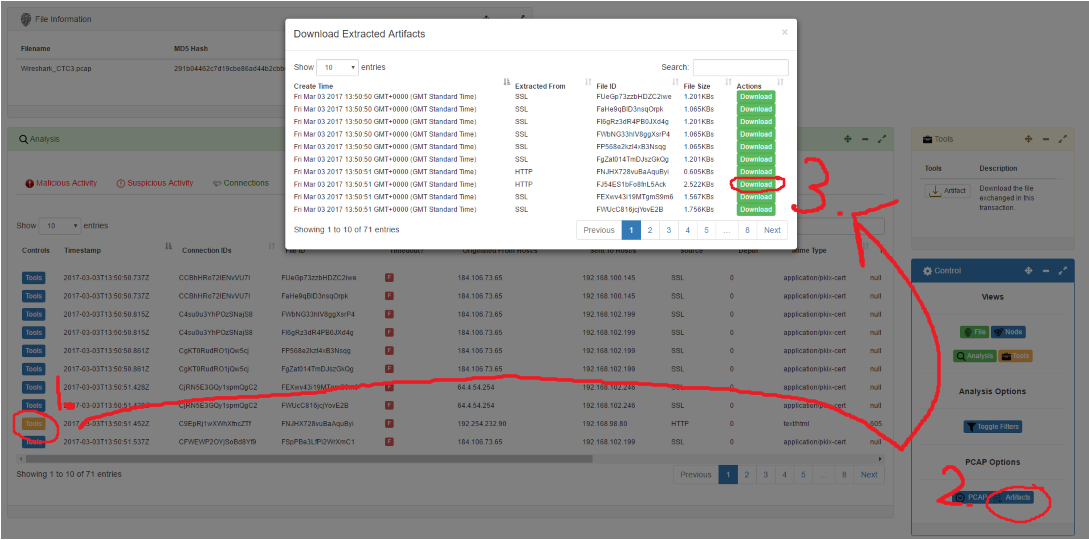
Using Network Miner
Windows GUI based high performance PCAP analyser from NETRESEC.
Ideal for quick image analysis / painting a picture of events and can even handle large PCAPs. Take note, you have limited performance due to the FREE version at 0.83Mbits/s so it might take a while to churn those larger PCAPs.
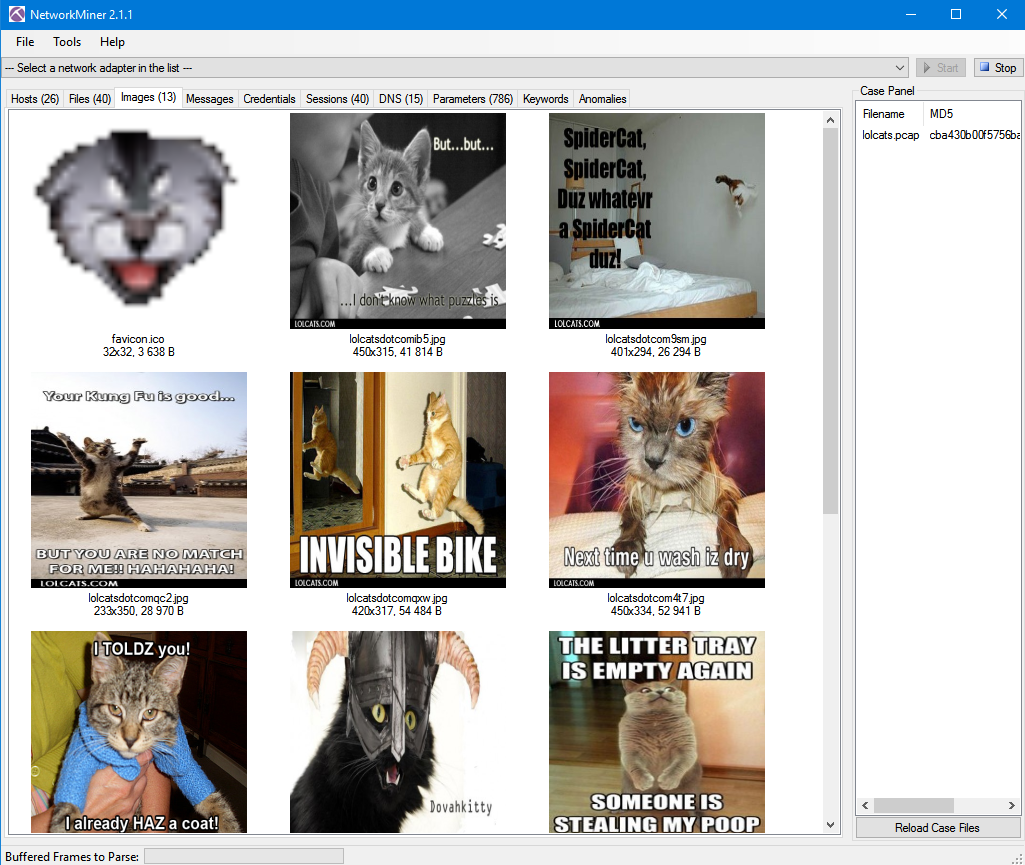
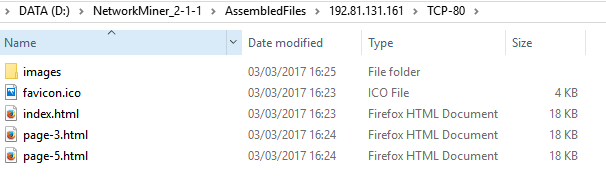
Network Miner automatically extracts and dumps the files into folders by IP.
Using either or all, each tool has their benefits and downfalls. Some are handy to have running automatically, others for are geared towards ad-hoc analysis. With so many tools out there its best to pick a few to master. For those hardcore enough custom Python/Scapy scripts will probably be the best.
Further Research
- SANS Reading Room https://www.sans.org/reading-room/whitepapers/forensics/extracting-files-network-packet-captures-36562
- Bro IDS Extraction Scripts https://github.com/hosom/bro-file-extraction
- Awesome-pcaptools list https://github.com/caesar0301/awesome-pcaptools
- Foremost http://tools.kali.org/forensics/foremost
- Xplico http://www.xplico.org/ http://tools.kali.org/information-gathering/xplico
- Scalpel https://github.com/sleuthkit/scalpel
- Scapy http://www.secdev.org/projects/scapy/


